Slave to the Game
Online Gaming Community
ALL WORLD WARS
FINDING, FIXING, AND FINISHING THE GUIDELINE:
The Development of the United States Air Force Surface-to-Air Missile Suppression Force During Operation Rolling Thunder
by Major John J. Deeney IV

F-105s Thunderchief take off on a mission to bomb North Vietnam, 1966.
During Operation Rolling Thunder, the United States Air Force was unprepared for the introduction of the SA-2 Guideline surface-to-air missile system into the North Vietnamese integrated air defense system (IADS). Following a series of aircraft losses in the summer of 1965, the USAF identified an emerging time critical requirement for a dedicated SAM suppression capability. This thesis will provide background for USAF air operations during Rolling Thunder. Next this thesis will use the Find, Fix, Finish, Exploit, and Analyze (F3EA) targeting methodology as an interpretive model for analyzing the creation, fielding, and tactical employment of USAF "Wild Weasel" platforms. This thesis will then analyze the structure and effectiveness of the North Vietnamese IADS, and show how mobility tactics and integration drove the requirement for the Wild Weasel platform. This thesis will discuss the initial acquisition and development of the Wild Weasel program up to and including the Wild Weasel III platform (F-105F/G), and then will examine how the operations-intelligence cycle allowed US aircrew to refine their understanding of the capabilities of the North Vietnamese IADS, and its emerging tactics. This thesis will conclude with an assessment of the Wild Weasel program during Rolling Thunder, and recommendations for future offensive counter-air planning and execution.
This effort has been greatly aided by the mentorship and feedback provided by a diverse team of friends, peers, and instructors that focused me through the research and writing process.
First I would like to acknowledge the members of my thesis committee- Maj Dean Balstad, LCDR Charles Paquin, and especially my committee chair, Dr. John Kuehn. These gentleman provided advice and feedback as well as encouragement and enthusiasm for my project. I am deeply indebted to them for their mentorship and counsel.
Next I would like to acknowledge Dr. Carol Reardon and Dr. Jackson Spielvogel (retired) of the Penn State History Department. Many years ago, these professors made a lasting impression on this undergraduate aerospace engineering major. Their expertise and passion opened my eyes to the study of history, and indirectly shaped my development as an officer in the United States Air Force. Additionally, I would like to thank Dr. Ethan Rafuse for his expertise and enthusiasm teaching the members of Staff Group 21 during CGSC Class 10-01. I am grateful to all three for their life-long impact on my development as an officer and as a student of history.
Most importantly I would like to thank my wife Heather and my daughters Haeley and Payton for their never-ending encouragement and support. Their love , their sense of humor, and their occasional insistence that Daddy stop working on his thesis and get off of the computer was instrumental in helping me tackle this project. They are the most important people in my life, and they continue to amaze me every single day.
AAA Anti-aircraft artillery
AB Air base
AFSS Air Force Security Service
AGI Auxiliary general intelligence
AGL Above ground level
ARM Anti-radiation missile
ASCAT Anti-Surface to air missile combat assessment team
AW Automatic weapons
C2 Command and control
CCD Camouflage, concealment, and deception
COMINT Communications intelligence
CSS Central Security Service
DCA Defensive counter-air
DMOB Defensive missile order of battle
DRV Democratic Republic of Vietnam
EA Electronic attack
ECM Electronic counter-measures
ELINT Electronic intelligence
EOB Electronic order of battle
EW Electronic warfare
EWO Electronic warfare officer
F3EA Find, fix, finish, exploit, analyze
FISINT Foreign instrumentation signals intelligence
GCI Ground controlled intercept
HF Height finder
HF High frequency
IADS Integrated air defense system
IC Intelligence community
IMINT Imagery intelligence
IPIR Initial Phase Imagery Report
ISR Intelligence, Surveillance, and Reconnaissance
JCS Joint Chiefs of Staff
LWR Launch warning receiver
MF Medium frequency
MiG Mikoyan Gurevich
MiGCAP MiG combat air patrol
MISREP Mission report
NSA National Security Agency
OCA Offensive counter-air
OEF Operation Enduring Freedom
OIF Operation Iraqi Freedom
OPREP Operations Report
PACAF Pacific Air Forces
PPIF Photo processing and interpretation facility
PRF Pulse repetition frequency
RHAW Radar homing and warning
RITS Reconnaissance intelligence technical squadron
RMA Revolution in military affairs
RTS Reconnaissance technical squadron
SAC Strategic Air Command
SADS-1 Soviet air defense system-1
SAM Surface to air missile
SEAD Suppression of enemy air defenses
SEE-SAMS See, exploit, evade SAMs
SIGINT Signals intelligence
STARM Standard ARM
TACRECCE Tactical reconnaissance
TACRISE Tactical Reconnaissance Intelligence System Enhancement
TOT Time on target
TTPs Tactics, techniques, and procedures
U.S. United States
USAF United States Air Force
USN United States Navy
USPACOM United States Pacific Command
USSR Union of Soviet Socialist Republics
VC Viet Cong
VHF Very high frequency
VISOBS Visual observers
CHAPTER 1. BACKGROUND
Introduction
Operation Rolling Thunder was the code name for the United States' strategic bombing effort against the Democratic Republic of Vietnam (DRV). Prior to the terrorist attacks of 11 September 2001, the Rolling Thunder campaign was the longest air campaign ever waged by the United States. Rolling Thunder forces fought in the skies of North Vietnam from March 1965 through April 1968. In April 1968 President Lyndon B. Johnson ordered a bombing halt against North Vietnam. Offensive air operations against the DRV would cease until the commencement of Operation Linebacker I in 1972, and continue until the termination of Operation Linebacker II and the end of US involvement in the Vietnam War.
Since the attacks of 11 September 2001, the US has executed longer air campaigns in support of both Operation Enduring Freedom (OEF) and Operation Iraqi Freedom (OIF). Unlike Rolling Thunder however, these campaigns have been conducted in a permissive threat environment where fixed wing aircraft operate with virtual impunity from threats. In the cases of both OEF and OIF, coalition air forces were able to quickly disrupt and dismantle enemy air defenses resulting in no fixed wing losses due to the enemy integrated air defense system (IADS).[1] The IADS suppression tactics used successfully during the opening phases of OEF and OIF have their origins in the Rolling Thunder campaign of 1964-1968. Because of this historical lineage, any understanding of current air power doctrine and tactics should consider the conduct of the Rolling Thunder campaign.
One focus area within the context of the broader Rolling Thunder campaign is the development of a dedicated surface-to-air missile (SAM) suppression force. The development of this force was spurred by the lethal and rapid evolution of the North Vietnamese integrated air defense system (IADS). The introduction of the SA-2 GUIDELINE missile into the DRV IADS in 1965 was a game-changer which forced a significant shift in American force packaging and tactics. This evolution generated a time-critical requirement for the USAF to develop a dedicated SAM suppression force. This force needed to be able to identify and locate SAM activity in real time, and operated as part of a loose network to find (detect), fix (locate), and finish (suppress or destroy) North Vietnamese surface to air missile sites in order to increase survivability and bombing effectiveness of strike packages operating over North Vietnam.
This thesis will analyze how the USAF developed its SAM-suppression network during Operation Rolling Thunder. Using the contemporary Find, Fix, Finish, Exploit, and Analyze (F3EA) targeting cycle as an interpretive model, this thesis seeks to enrich our understanding of SAM suppression development in Vietnam in order to draw conclusions enabling more effective air operations in the future. A secondary area for analysis is to examine how the SAM suppression force developed its understanding of North Vietnamese IADS capabilities, and make conclusions to enable enhanced IADS understanding in future conflicts.
Significance
Current Joint and USAF doctrine describe counter-IADS operations as the primary focus of the counter-air mission set. According to Joint Publication 3-01, "The purpose of counter-air is to attain the desired degree of air superiority required by the Joint Force Commander to accomplish the assigned mission."[2] Counter-air consists of both offensive counter-air (OCA) and defensive counter-air (DCA). OCA is defined as "offensive operations to destroy, disrupt, or neutralize enemy aircraft, missiles, launch platforms, and their supporting structures and systems both before and after launch, but as close to their source as possible. The goal of OCA operations is to prevent the launch of enemy aircraft and missiles by destroying them and their overall supporting infrastructure prior to employment. This could mean preemptive action against an adversary."[3] Current offensive-counter-air tactics, techniques, and procedures (TTPs) trace their origins to the Rolling Thunder campaign over North Vietnam. Understanding the historical development of those TTPs, and focusing on the integration of varied reconnaissance, surveillance, and strike assets into an effective network will help current planners and tacticians avoid historical pitfalls. Additionally, contemporary operations in Iraq and Afghanistan have demonstrated the success of the F3EA model and operations- intelligence fusion. This historical review of the SAM suppression problem seeks to demonstrate the applicability and suitability of the F3EA model to contemporary counter- IADS operations.
The Origins of Operation Rolling Thunder
In the spring of 1964, the Joint Chiefs of Staff (JCS) and US Pacific Command (USPACOM) commenced planning for the possibility of a bombing campaign against North Vietnam. This planning effort resulted in the selection of 94 targets in North Vietnam including transportation, industrial, and infrastructure targets.[4] This target list would eventually serve as the primary targeting effort during the Rolling Thunder campaign.
Prior to the onset of Rolling Thunder, the US conducted a series of reprisal strikes against North Vietnam. Following the Gulf of Tonkin incidents in early August 1964, the US launched the Pierce Arrow strikes in retaliation for purported North Vietnamese attacks on US Navy destroyers operating in the Tonkin Gulf. These strikes took place on 5 August 1964. The Pierce Arrow strikes were flown by United States Navy (USN) carrier based aircraft operating from the Gulf of Tonkin. The Pierce Arrow strikes targeted four torpedo boat bases, and oil storage facilities near Vinh, North Vietnam. The strikes succeeded in destroying eight PT boats, damaging twenty-one, and destroying nearly 90 percent of the oil facility at Vinh. USN losses during the strike included an A-4 Skyhawk and an A-1 Skyraider shot down by anti-aircraft artillery (AAA) fire, resulting in one pilot killed in action, and another pilot captured by the North Vietnamese.[5] Following the Pierce Arrow strikes, President Johnson succeeded in getting Congress to pass the Gulf of Tonkin Resolution, which underpinned the subsequent escalation of the US war effort against North Vietnam.[6]
The pattern of North Vietnamese or Vietcong action and US counter-action continued through the rest of 1964 into 1965. In February 1965, following Vietcong attacks on US bases in South Vietnam, President Johnson ordered retaliatory air strikes, code-named Operation Flaming Dart I and Operation Flaming Dart II. The Flaming Dart strikes marked a turning point in the air war against North Vietnam, and the following month Operation Rolling Thunder commenced against North Vietnam. Rolling Thunder would continue until the bombing halt of 1968.
The Context of Operation Rolling Thunder
Gradualism, and Constraints
The Rolling Thunder campaign was, and still is, controversial. In order to understand the broader context of Rolling Thunder, one must always consider the backdrop of the Cold War. US foreign policy viewed communism as a monolithic entity, intent on challenging US interests around the globe. In Vietnam, the US always considered the implications of tactical and operational actions in Vietnam as they related to the potential of all-out war with either the USSR or China. This concern, lead to the concept of gradualism which typified the Rolling Thunder campaign.
Rolling Thunder was approved by President Johnson in February 1965 as "a program of measured and limited air action jointly with the government of Vietnam against selected military targets in the DRV."[8] The strict limitations placed on air operations against North Vietnam were intended to minimize the potential for Chinese or Soviet active involvement in the conflict and to maximize the opportunity for the North Vietnamese to capitalize on peace initiatives. In actuality, these limitations resulted in a situation that completely ceded the initiative to the North Vietnamese. President Johnson used "bombing pauses" as a carrot to entice the North Vietnamese to the peace initiative, but the North Vietnamese used the bombing pauses instead to repair and refit forces for follow-on combat operations.
Unlike previous air campaigns, the Rolling Thunder campaign objectives were nebulous and difficult to quantify. The campaign objectives for Rolling Thunder were:
1. To reduce DRV and Vietcong (VC) activities by affecting their will
2. To improve morale of the South Vietnamese forces
3. To provide the US bargaining leverage
4. To reduce the infiltration of men and material into South Vietnam
5. To demonstrate the US's willingness to fight for an ally.[9]
Of the five campaign objectives, only the infiltration of men and material into South Vietnam provided an objective with a quantifiable metric. Over time, this interdiction effort became the main effort for the Rolling Thunder campaign.
Command and Control Challenges
The command and control arrangement for Operation Rolling Thunder further exacerbated the significant challenges posed by the policy of gradual escalation and extreme tactical and operational constraint exercised by national level leadership in Washington, D.C. The overall direction of Operation Rolling Thunder was set by the Commander, U.S. Pacific Command (USPACOM). The PACOM commander exercised command through both Pacific Air Forces (PACAF) and Pacific Fleet (PACFLT). PACAF's primary operational level headquarters was 2nd Air Division which was later replaced by 7th Air Force. PACFLT exercised command through Commander Task Force 77 (CTF-77). Air Force and Navy responsibilities under Operation Rolling Thunder were geographically de-conflicted using the Route Pack system developed in late 1965. Under the Route Pack system, North Vietnam was divided into 7 geographic areas, with each area assigned to a specific service. Route Packs were numbered I through VI, with route pack VI split into pack VIA and VIB along the Northeast railroad line to China. The USAF was responsible for operations in Route packs I, V, and VIA. The USN was responsible for route packs II, III, IV, and VIB (see figure 1).[10] The highest threat route packs were packs IV, V, and VI. The most dangerous area of North Vietnam was the Red River Valley, covered by Route Pack VI.
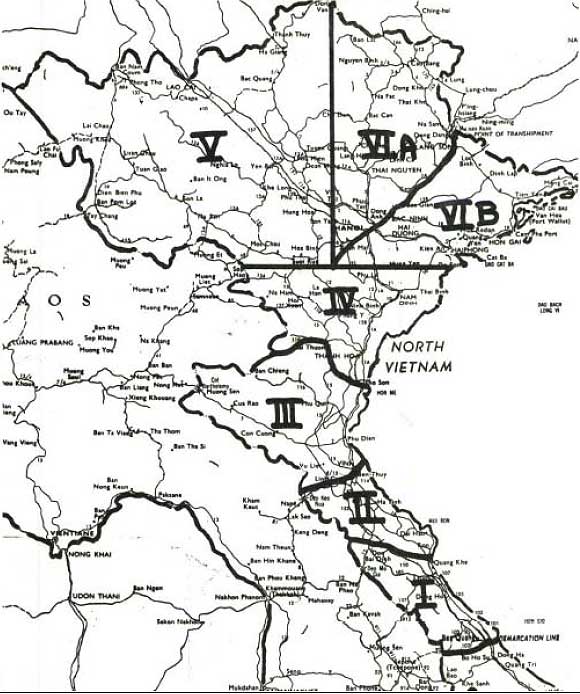
Figure 1. The Route Pack System
Source: Wesley R. C. Melyan, and Miss Lee Bonetti, PROJECT CHECO REPORT: Rolling Thunder July 1965-December 1966 (HQ PACAF, 1967), 41.
The Beginnings of Rolling Thunder During the first three months of Rolling Thunder, strikes against the approved JCS targets were able to operate somewhat successfully with a low loss rate. Air forces striking targets in North Vietnam operated at medium altitude, which allowed them to stay out of the heart of the DRV's air defense system, which consisted of a relatively rudimentary mix of automatic weapons, AAA, a minimal early warning (EW) network, and a limited number of primitive air interceptors. The medium altitude sanctuary, encompassing altitudes between approximately 5,000 feet AGL to 30,000 feet AGL, was denied to US air forces beginning on 24 July 1965 when an F-4C Phantom became the first USAF aircraft lost to an SA-2 Guideline SAM system over North Vietnam. Following this shoot-down, the USAF realized it needed to rapidly develop a capability to suppress or destroy DRV SAMs.
The F3EA Cycle
Combat operations in both OEF and OIF are typified by direct action raids to kill or capture insurgents and terrorists. In effect, combat operations in Afghanistan and Iraq are man-hunting efforts to disrupt and destroy insurgent and terrorist networks, destroying their ability to fight. In order to execute this counter-network effort, US forces have developed a task-oriented air-ground team to conduct these operations. This air- ground task force combines airborne Intelligence, Surveillance, and Reconnaissance assets with air and ground based striking-forces. A key to success of this counter-network operation is a dynamic targeting cycle that is known as "F3EA: Find, Fix, Finish, Exploit and Analyze" (see figure 2).[11] The remainder of this chapter will describe why this cycle lends itself to analysis of the Rolling Thunder air campaign, focused on the development and tactical implementation of a dedicated SAM suppression force.
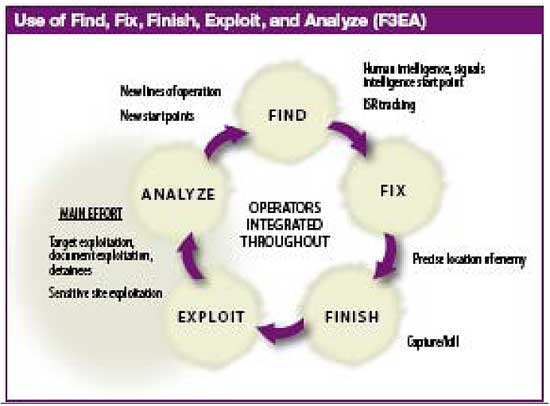
Figure 2. The Find, Fix, Finish, Exploit, and Analyze Cycle
Source: Michael Flynn, Rich Juergens, and Thomas Cantrell, "Employing ISR: SOF Best Practices," Joint Forces Quarterly (2008): 57.
The F3EA methodology provides a simple, flexible model for conducting
counter-network operations against a "low-contrast" and mobile enemy. As will be demonstrated in chapter 2, the North Vietnamese SAM force was a low-contrast (i.e. highly reliant on camouflage, concealment, and deception), mobile enemy, that operated as part of the greater DRV IADS network. The F3EA cycle begins with the find phase during which US forces are searching to identify targets within the network. The find phase requires all source intelligence analysis fused with the latest operations derived intelligence. This operations-intelligence fusion is the engine that drives the F3EA cycle, and is one of the critical requirements for its success in combat.[12] Fixing the enemy requires the task-force to develop increasingly accurate geo-locational data on a target in order to mass Intelligence, Surveillance, and Reconnaissance (ISR) forces against the target, better develop understanding of the target and its pattern of life, and position the task-forces' striking force to act decisively against the target when able. A key concept that enables the Find/Fix phases is the concept of persistent ISR. Persistent ISR, coupled with a never-ending operations-intelligence fusion and analysis effort creates an "unblinking eye" which limits the adversaries' freedom of movement and enables conditions for follow-on finishing operations.[13]
Unlike other targeting models, the F3EA model differs because it places the main effort for the counter-network operation on the exploitation and analysis of operational intelligence. The F3EA exploitation and analysis effort enables a task force to gain a detailed understanding of the threat network. This understanding is then used to identify potential targets (find) and then develop timely and accurate geo-locational data (fix) in order to capture or kill (finish) members of the network.[14] Another nuance to the F3EA cycle is that finishing operations do not always require the successful capture/killing of the target in order to be successful. In F3EA, the finishing operation is equally focused on producing intelligence to lead follow-on operations. The interaction of the finishing force with the threat network has the potential to produce actionable intelligence for follow-on operations.[15] This was particularly true of the Rolling Thunder SAM suppression force, which always attempted to better understand the North Vietnamese SAM force and IADS through the operations-intelligence cycle that was part of each combat mission.
F3EA Applied to SAM Suppression in Rolling Thunder
In order to use F3EA as an interpretive model for understanding the development of SAM-suppression forces during Rolling Thunder, this thesis will first examine the DRV integrated air defense system. By examining the structure, function, and adaptations of the North Vietnamese IADS, this thesis will demonstrate the importance of mobility to IADS survival, and highlight the need to establish a SAM suppression hunter/killer force. This force will be examined within the Find/Fix, Finish, and Exploit/Analyze model. Each function of the cycle will be examined in the context of SAM-suppression during Rolling Thunder. Using this model the thesis will draw conclusions about the utility of the F3EA model to counter-IADS operations in order to learn from history.
Chapter 2 will introduce the concepts necessary to understand basic IADS architecture and concepts, followed by a detailed discussion of the DRV IADS and its evolution during the Rolling Thunder campaign, with a focus on how the introduction and integration of the SA-2 into the IADS created the need for a dedicated SAM suppression force. Chapter 3 will analyze the development of the SAM suppression force using the find, fix, finish methodology. Chapter 4 will examine how the SAM suppression force used exploitation and analysis to complete the targeting cycle and enhance US understanding of the DRV IADS. Finally, chapter 5 will summarize the thesis and draw conclusions to help enhance air component suppression of enemy air defense (SEAD) capabilities in future conflicts.
[1]No fixed wing aircraft were lost to enemy fire during Operation Enduring Freedom. Two USAF A-10s were lost to ground fire associated with ground maneuver forces during the opening phase of Operation Iraqi Freedom. Air defense forces associated with ground maneuver forces are intentionally disassociated from the construct of the integrated air defense system.
[2]Joint Chiefs of Staff, Joint Publication 3-01, Countering Air and Missile Threat, (Washington, DC: Government Printing Office, 2007), ix.
[3]Ibid., x.
[4]Charles T. Kamps, "The JCS 94-Target List," Aerospace Power Journal (2001): 67-80.
[5]Jacob Van Staaveren, Gradual Failure: The Air War Over North Vietnam, 19651966 (Washington, DC: Air Force History and Museums Program, 2002), 49.
[6]H. R. McMaster, Dereliction of Duty: Lyndon Johnson, Robert McNamara, the Joint Chiefs of Staff, and the Lies That Led to Vietnam (New York: Harper Collins, 1972), 138.
[7]Van Staaveren 2002, 69.
[8]Department of Defense, The Pentagon Papers (Gravel Edition) Vol 3 (Washinton, DC: 1968), 1.
[9]Dennis Drew, Rolling Thunder 1965: Anatomy of a Failure (Maxwell AFB: Air University Press, 1986), 59.
[10]Wesley R. Melyan, and Miss Lee Bonetti, PROJECT CHECO REPORT: Rolling Thunder July 1965-December 1966 (HQ PACAF, 1967), 39.
[11] Michael T. Flynn, Rich Juergens, and Thomas L. Cantrell, "Employing ISR: SOF Best Practices," Joint Forces Quarterly (2008): 57.
[12]Ibid.
[13]Ibid., 58.
[14]Ibid., 60.
[15]Ibid.
CHAPTER 2. NORTH VIETNAM'S INTEGRATED AIR DEFENSE SYSTEM
Introduction
The origins of an IADS can be traced to the development of the Chain Home system in the United Kingdom during World War II. An IADS is a network consisting of sensors, weapons, and command and control (C2) designed and employed to defend a country or area from aerial attack. During the Cold War, the Soviet Union developed an advanced IADS to defend the homeland from attack. Soviet air defense equipment and aircraft were exported throughout the Soviet Block. When the US began air operations against the Democratic Republic of Vietnam (DRV) in August 1964, they faced a relatively small and undeveloped North Vietnamese IADS.
In November 1964, Soviet Premier Leonid Brezhnev and the Soviet Politburo approved a significant increase of aid, advisors, and weapons to the DRV.[1] This marked a significant increase in Soviet involvement and aid to the DRV. New weapons, including the SA-2 Guideline, were offered to the DRV. In addition to the SA-2 SAM system, the Soviets increased capability and capacity of other air defense sensors and weapons. In addition to material support, the Soviets provided the necessary training for the North Vietnamese air defense crews. Select North Vietnamese personnel were sent to the Soviet Union for training on weapons and tactics. Additionally, the Soviet Union began sending advisors to the DRV to help the North Vietnamese establish their fledgling air defense force and to provide continuation training.
As US air operations against the DRV continued into 1965, US forces were met by an increasingly capable IADS that was in the process of integrating new sensors and weapons. Throughout the Rolling Thunder campaign, the DRV IADS developed from a back water air defense system into the most lethal, concentrated, and combat experienced IADS ever faced by US air forces.
IADS Structures and Functions
In order to discuss the DRV IADS in detail, one must first understand the basics of IADS structure and functions. From a structural perspective, a modern IADS consists of three key components: sensors, weapons, and a command and control (C2) architecture. From a functional perspective, an IADS carries out three necessary functions: air surveillance, battle management, and weapons control. In order to analyze the DRV IADS, this study will examine both structural and functional aspects of the IADS as they existed during Rolling Thunder.
Sensors and The Air Surveillance Function
The DRV IADS consisted of a mix of active and passive sensors that enabled DRV air defense commanders to build an air picture of U.S. air operations. These sensors work as part of an integrated network to develop a national air picture. This air picture serves as the common operating picture for overall IADS situational awareness and decision making.
In order to develop the air picture, the DRV relied primarily on active sensors including Early Warning (EW), Ground Controlled Intercept (GCI), and Height-Finder (HF) radars. EW, GCI, and HF radars provided the DRV long range capability, allowing the DRV to detect, identify, and track aircraft operating over the DRV as well as in surrounding airspace.
The DRV used Soviet Spoon Rest, Flat Face, and Tall King radars for EW purposes. For GCI purposes, the DRV used Token or Barlock radars.[2] These EW radars were deployed in order to provide overlapping coverage, resulting in increased detection capability for the IADS. DRV long range EW radars were typically able to detect US strike formations as they marshaled in aerial refueling tracks over northern Laos and the Tonkin Gulf.
The DRV also employed height finder (HF) radars including Rock Cake, Stone Cake, and Side Net. Height finders are long range radars that complement EW radars by providing elevation or altitude data on air tracks. Elevation data is a key discriminator in building the air surveillance picture as it helps the IADS identify tracks, as well as make battle management and weapons control decisions.[3]
In addition to active radar sensors, the DRV IADS also incorporated a robust passive sensor capability. Passive sensors included communications intelligence (COMINT) and electronic intelligence (ELINT) sensors used to monitor US activity. COMINT collectors consisted of ground based sensors that were able to monitor US air to air communications. COMINT collection allowed the Vietnamese to augment their air surveillance picture by monitoring call signs in order to identify the composition and intentions of strike packages.[4] ELINT monitoring allowed the Vietnamese to identify airframes based on radar or electronic countermeasures signatures. In addition to DRV organic capabilities, the DRV was also passed information from Soviet collection sources, especially from Soviet trawlers (AGIs) that monitored US 7th fleet activities, as well as USAF activity originating from Guam.
In addition to electronic sensors, the DRV employed a robust visual observation (VISOB) network throughout North Vietnam. VISOBs were able to relay aircraft activity throughout the IADS in order to provide early warning to the entire network. VISOBs did not always require visual detection of US air forces, and would often report detection of inbound raids based on jet noise alone. In 1965, the DRV maintained approximately 40 VISOB posts throughout North Vietnam, but that number would increase throughout the Rolling Thunder campaign.[5]
Together, this mix of active and passive sensors worked to develop a coherent air picture for the DRV IADS. The sensors, located at radar companies, would develop plots, or individual "hits" on US aircraft, which over time would be developed into tracks. These tracks would be passed up channels via the C2 network to a filter center, and/or passed laterally to a co-located weapons unit. The primary filter center was located at Bac Mai airfield in Hanoi.[6] The filter center existed to remove redundant tracks, or create tracks from spurious plots. In addition to serving as the filter center, Bac Mai also served as the national air defense command post. The process of filtering allowed the DRV to integrated various sensors and create a coherent air picture that enabled battle management decision making.
C2 and the Battle Management Function
C2 consists of the architecture necessary for the IADS to pass information and orders throughout the system. This information is used by battle managers to make decisions, and then communicate orders and status updates throughout the IADS. The DRV IADS used a mix of landline and radio communications links to pass information throughout the system. Landlines provided the DRV with a secure method of passing information, but the tradeoff was the requirement to lay lines, and the susceptibility of those lines to kinetic attacks. Radio links allowed increased mobility, but at the cost of security. Radio links used by the DRV IADS included very high frequency (VHF) voice as well as medium frequency (MF) or high frequency (HF) voice and manual Morse code. U.S. COMINT platforms were able to monitor DRV radio communications to provide threat warning as well as develop a detailed understanding of the IADS structure and processes.[8]
Effective C2 enabled the IADS decision makers to make the most effective and efficient judgments on how to defend the DRV's airspace. Because sensors were well integrated by the C2 architecture, the IADS as a whole was more effective than individual systems operating autonomously, or in isolation. This degree of integration was described by a Pacific Air Forces Electronic Warfare summary from 1966:
Radar, AAA, and SAMs began to display a high degree of discipline. The three systems were fully integrated under an excellent command and control net which, of necessity, extended to the fighter force also. This was a methodical, high caliber, tight control, multi-directional defense development, and it is significant to note that what took seven years to set up in the Soviet Satellite bloc, took but seven months (from April 1965 when the first SAM sites were photographed) in North Vietnam.[9]
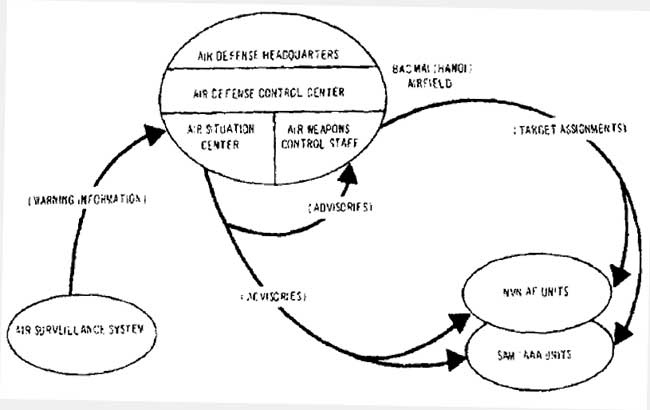
Figure 3. Simplified view of DRV IADS
Source: Robert J. Hanyok, Spartans in Darkness: American SIGINT and the Indochina War, 1945-1975 (Fort Meade, MD: Center for Cryptologic History, 2002), 237.
Weapons and Weapons Control
Prior to July 1965, the weapons used by the DRV IADS were representative of the type of threat that US air forces had faced during previous conflicts including the Korean War and World War II. Weapons included air interceptors or fighter aircraft, as well as anti-aircraft artillery (AAA). Air interceptors provided the DRV the longest-range capability to defend airspace, while AAA was useful for defense of key areas in either an area defense or point defense pattern.
The Air Interceptor Force
At the onset of Rolling Thunder, the DRV Air Force flew a mix of MiG-15 and MiG-17 aircraft The MIG-21 was incorporated into the DRV's inventory in late 1967, and the MiG-19 did not enter the DRV inventory until after the bombing (Linebacker I and II) was halted in 1972. North Vietnamese pilots were trained in Russia, and operated using Russian tactics. Russian air intercept doctrine placed the fighter pilot under the close control of a GCI controller, who directed the fighter to a hostile aircraft Close GCI control was necessary for North Vietnamese aircraft which lacked radars, and relied exclusively on guns and infrared missiles which required a visual acquisition to employ.
DRVAF airfields including Kep and Phuc Yen were the primary alert MiG bases during Rolling Thunder. DRV controllers typically employed fighters for use in "hit and run" attacks on US strike aircraft These tactics allowed the DRV to utilize the MiGs maneuverability and small size, while simultaneously capitalizing on the sanctuary status of their alert airfields. The airfield status was the direct result of constraints placed on US air forces by its civilian leadership, and yielded the initiative to the DRV.
The AAA Force
Throughout the history of aerial combat, ground fire has always been the leading cause of combat losses. This fact remained true throughout the Rolling Thunder campaign. DRV AAA consisted of a wide range of weapons ranging from automatic weapons (AW) up to 100 mm AAA which could range targets in excess of 40,000 feet above ground level (AGL). AAA was employed using both optical and radar directed tracking techniques.
At lower altitudes, the primary threat came from automatic weapons, which included AAA down to 12.7mm, as well as 14.5mm and 23mm weapons systems. These weapons were often optically directed, had high rates of fire, and could threaten aircraft operating below 6,000 feet AGL. Larger caliber weapons systems including 37mm and 57mm AAA were also optically directed, but could be directed by gun laying radars as well. Gun laying radars, like FIRECAN, were used to direct batteries of AAA towards a specific target, and provided tracking data that included target altitude.[10] Target altitude was used by the AAA batteries to tailor fuse settings in order to maximize the likelihood that AAA would fuse in close proximity to the target altitude. Finally, larger caliber AAA included 85mm and 100mm batteries that could range targets up to approximately 40,000 ft AGL. This mix of both optically and radar directed AAA created a lethal threat envelope that could range targets up to 40,000 feet, with the densest concentration of AAA creating a lethal engagement area up to approximately 10,000 feet AGL.
AAA was concentrated along known ingress routes for US strike aircraft, as well as in the vicinity of key DRV targets including airfields, power plants, railways and rail yards, and bridges. The majority of the DRV's key infrastructure was in the Red River Valley and near the cities of Hanoi and Haiphong. Due to the small geographic area of the Red River Valley, the concentration of AAA during Rolling Thunder created the densest concentration of AAA ever faced by U.S. air forces. U.S. forces were able to mitigate the robust AAA threat during the initial months of Rolling Thunder by operating at medium altitude, typically between 10,000-20,000 feet AGL. This medium-altitude block provided U.S. aircraft with enhanced survivability, while still allowing U.S. forces the ability to bomb targets accurately using dive-bombing attacks from medium altitude.
However, with the introduction of the SA-2 GUIDELINE into the DRV inventory in the summer of 1965, U.S. medium altitude tactics quickly became obsolete.
The SAM Force
As Rolling Thunder began in the spring of 1965, the DRV lacked surface-to-air missiles in their inventory. The primary SAM in use throughout the Soviet block was the SA-2 Guideline. The USAF and the intelligence community (IC) had been aware of the SA-2 since it became operational in the USSR in 1957. The SA-2 was thrust to the forefront of international attention when Francis Gary Powers was downed by an SA-2 in May 1960. Powers was flying a U-2 on an intelligence collection mission near the Soviet town of Sverdlosk, when he was shot down while flying at 65,000 feet. This shoot down, and Powers subsequent internment in a Soviet prison brought about the end of the U-2 over flight program of the Soviet Union. Later, during the Cuban Missile Crisis, Maj Rudolph Anderson was shot down by an SA-2 while conducting a reconnaissance mission over Cuba in November 1962.[11] Thus, at the onset of Rolling Thunder operations in March 1965, the U.S. was well aware of the threat posed by the SA-2, but as will be demonstrated, was ill prepared to deal with it.
The SA-2 Guideline Weapon System
The SA-2 is a road-transportable strategic surface-to-air missile system. A doctrinal SA-2 battalion (firing unit) consists of a single Fan Song radar set, a computer van, a control van, generator van, six missile launchers with Guideline missiles, missile trans-loaders with missile reloads, and a mix of various support vehicles. Additionally, SA-2 battalions often had a co-located EW radar working in a direct-support acquisition role. The DRV typically used the Spoon Rest radar in this capacity. In total, an SA-2 Battalion consisted of approximately 25 vehicles. Tactical control of the battalion was exercised by a seven man crew that operated from the control van. This tactical crew consisted of a battalion commander, three guidance officers, a plotter, a fire control officer, and a missile control officer.[12]
The Guideline was a large missile - approximately 35ft long, and weighing close to 5,000 lbs. The Guideline provided the SA-2 system a lethal range out to approximately nautical miles and up to 83,000 feet. The system had a dead zone of approximately 5 nautical miles centered on the site, due to maneuver limitations of the missile while it was in its boost phase. The Guideline missile travelled at nearly Mach 4, and had a lethal burst radius of 150-200 feet. The system was capable of engaging targets down to approximately 3,000 ft AGL. This altitude limitation was due to the Fan Song radar's inability to track targets lower than that altitude.[14]
The SA-2 is a command guided system. In a command guided system the radar tracks both the target and the missile. The system computes guidance commands on the ground, and then transmits those commands to the missile in flight. The missile executes those commands to complete the intercept of the target. The Fan Song was a track while scan radar system that used perpendicular azimuth and elevation beams to center the radar's scan volume on the assigned target. The Fan Song tracked the target in both azimuth and elevation based off of raw radar returns from the target. The missile was passively tracked by a beacon transmitter on the aft end of the Guideline missile. Based on the relative geometry of the missile and the target, the system computed guidance commands for the missile to fly. These guidance commands were transmitted to the missile via a separate missile guidance antenna. This guidance signal was referred to by US aircrew and intelligence personnel as the missile uplink, and consisted of a series of coded pulses. The uplink was received by the Guideline missile in flight, and the missile executed steering commands to complete the intercept.[15]
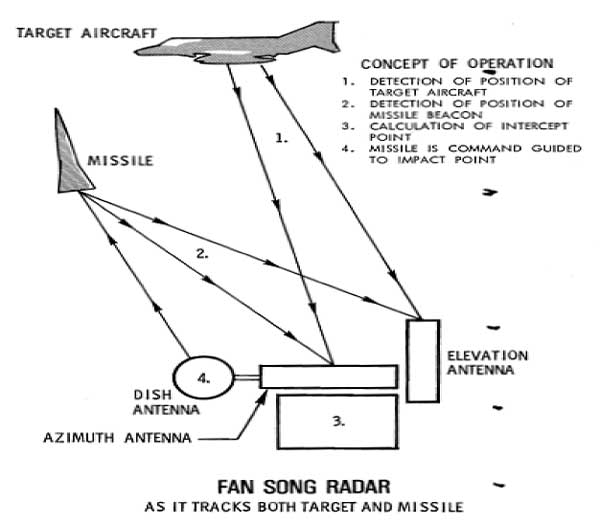
Figure 4. Fan Song Concept of Operations
Source: Bernard Nalty, Tactics and Techniques of Electronic Warfare: Electronic Countermeasures in the air War Against North Vietnam 1965-1973 (Washington, DC: Office of Air Force History, 1977), 5.
The SA-2 battalion was most effective when integrated into the overall IADS. The SA-2 battalion started its engagement process by receiving track data from higher headquarters. This track data normally consisted of a track number, a location passed in grid or polar formats, and if available, an altitude estimate.[16] Track data was typically passed via landline, if available, or via VHF voice radio transmissions. [17] This track tipoff allowed the SA-2 battalion commander to attempt to acquire the assigned target. The plotting officer would manually update the plotting board in the control van, while at the same time the battalion commander was attempting to acquire the track using the co-located Spoon Rest radar. Once the track was detected, the battalion could transmit from the Fan Song and attempt to acquire the target and begin the engagement process.[18] When the battalion operated without the aid of acquisition radar, or was cut-off from IADS cueing, it could still self-acquire using the Fan Song, but this was a degraded (autonomous) mode of operation. By 1965 the tracking process, from initial EW detection to Fan Song handoff, was completed in less than 5 minutes.[19]
The SA-2 battalion would transmit using the Fan Song in an attempt to acquire the target. The process of acquisition, target tracking and missile launch took approximately 75 seconds.[20] The missile was launched towards a predicted intercept point in front of the target. During the first four seconds of flight, the missile was flying on a ballistic path while the booster accelerated the missile. After four seconds, the booster fell off, exposing the missile beacon and uplink antenna, at which point the missile would begin to maneuver. The boost phase was significant because it provided aircrew the greatest probability of visually detecting the missile in flight. The launch typically kicked up a large cloud of dust, and the booster's significant exhaust plume was easy to detect. Once the booster was jettisoned, the visual detection of the Guideline became more difficult.[21] As the Guideline approached the target, its radar proximity fuse was enabled, along with the backup impact fuse. The Guideline would fuse on the target, creating a lethal burst radius of 150 to 200 feet. The SA-2 did not have to kill its assigned target to be effective. By denying US fighter aircraft the ability to operate at medium altitude, US fighter aircraft would descend to low altitude, where they often fell prey to the layered threat presented by the DRV's dense AAA force.
The Introduction of the SA-2 Into North Vietnam
Following the Soviet decision in late 1964 to increase air to the DRV, the Soviets began an in-country training program for DRV air defenders to begin their familiarization with the SA-2 system. On 5 April 1965 a U-2 mission over the DRV detected the first SA-2 site under construction near Hanoi. The site construction was similar to Soviet site layout. Immediately the JCS urged the destruction of the site, before it became operational. This request was denied by the civilian leadership in Washington, D.C.
Between April and July 1965, reconnaissance aircraft detected the construction of five additional SAM sites in a ring around Hanoi. On 7 July 1965 General John McConnell, Chief of Staff of the Air Force, briefed the administration that the sites could be operational within 48 hours. Still, the administration denied JCS requests to strike the sites. [22]The civilian leadership in Washington felt that the DRV would never use the SA- 2s against US aircraft Assistant Secretary of Defense John McNaughton was reported to have remarked that "you don't think they'll actually use them?," and that the SA-2 was only a ploy being used by Hanoi. During an 11 July press conference, Secretary of State Dean Rusk announced that there was no plan "at this time" to strike the SAM sites. [23]This lack of critical thought by the national leadership would lead to disaster on 24 July 1965, when the SA-2 made its first kill of the Vietnam war, and claimed the first of many airmen's lives to come.
On 23 July 1965, an RB-66C detected Fan Song ELINT activity from a previously undetected site 23 nm west of Hanoi. This activity was analyzed and briefed to strike crews during their pre-mission briefings on 24 July. At 0850Z on 24 July 1965, orbiting RB-66Cs again noted Fan Song ELINT approximately 20nm west of Hanoi, and relayed this warning to strike packages and escorts in the vicinity of Hanoi. Shortly after this, Leopard flight, a flight of F-4Cs flying MiG combat air patrol (MiGCAP) for strikers, noted multiple missiles closing on the flight. The flight, operating in poor weather, was in close formation. The detonation of the SA-2 destroyed one of the F-4Cs, Leopard 02, and damaged the rest. [24]The crew of Leopard 02 consisted of Captain Roscoe Fobar and Capt Richard Keirn. Capt Fobar was killed in action, and Capt Keirn spent the rest of the war in captivity in Hanoi. [25]The SA-2 had drawn first blood in Operation Rolling Thunder.
The First SAM Suppression Strike
On 28 July, the JCS authorized a strike against the sites suspected of engaging Leopard flight on 24 July. The strike force consisted of 54 aircraft including strikers, flak suppressors, escorts, and ELINT support. Ingress headings, altitudes, airspeeds, and weapon load outs were all specified by the air tasking order, and the strike force was not allowed to make any changes to the specified plan. The strike force consisted of two packages of aircraft from both Takhli AB and Korat AB. The directed weapons load out consisted of napalm canisters, high drag unitary bombs, and CBU-2 cluster bombs. The CBU-2 was especially problematic, as it was a rear-dispensing bomblet dispenser that required the strike aircraft to directly overly the target. The force ingressed to the target area at 50 feet AGL, as specified by the order and delivered their ordnance on the target area. It was immediately clear to the strike force that dummy equipment had been emplaced at the site, and the North Vietnamese were waiting with a flak-trap.[26] The low altitude ingress into the flak-trap resulted in the loss of six F-105s-nearly 10 percent of the strike force. Three F-105 pilots were killed, two were captured, and only one was rescued.[27] The disastrous strike was a watershed moment in US tactical air operations, and would lead to the rapid development and employment of dedicated SAM suppression airframes and tactics.
[1]Merle L. Pribbenow, "The -Ology War: Technology and Ideology in the Vietnamese Defense of Hanoi, 1967" Journal of Military History (2003): 177.
[2]Charles H. Heffron Jr., PROJECT CHECO REPORT: Air to Air Encounters Over North Vietnam, 1 January-30 June 1967 (HQ PACAF, 1967), 5-6.
[3]Ibid.
[4] Robert J. Hanyok, Spartans in Darkness: American SIGINTand the Indochina War, 1945-1975 (Fort Meade, MD: Center for Cryptologic History, 2002), 252.
[5]Ibid., 235.
[6]John C. Pratte, PROJECT CHECO REPORT: USAF Tactics Against NVNAir Ground Defenses December 1966-November 1968 (HQ PACAF, 1969), 14.
[7]Ibid.
[8]Hanyok, 237.
[9]Robert M. Burch, PROJECT CHECO REPORT: Tactical Electronic Warfare Operations in SEA, 1962-1968. (HQ PACAF, 1969), 25-26.
[10]Bernard Nalty, Tactics and Techniques of Electronic Warfare: Electronic Countermeasures in the air War Against North Vietnam 1965-1973. The Air Force in Southeast Asia Monograph Series (Washington, DC: Office of Air Force History, 1977), 7.
[11]Ibid., 2.
[12] Marshal L. Michel III, The Eleven Days of Christmas: America's Last Vietnam Battle (San Francisco: Encounter Books, 2002), 93.
[13]Pratt, 1.
[14]Nalty, 2-4.
[15]Michel, 106.
[16]Hanyok, 238.
[17]Ibid., 237.
[18]Michel, 94.
[19]Hanyok, 238.
[20]Nalty, 4.
[21]Ibid., 49.
[22] Van Staaveren, 113. 23Ibid., 161. 24Bonetti, 3. 25Staaveren, 161.
[26]Bonetti, 3.
[27] Edward T. Rock, First In Last Out: Stories by the Wild Weasels (Bloomington, IN: Authorhouse Books, 2005), 4, 19.
CHAPTER 3. FIND, FIX, FINISH
The Problem of SAM Mobility The results of the disastrous Iron Hand 1 mission quickly demonstrated to US air commanders the unique problem presented by the adaptation of rapid SAM mobility tactics coupled with highly effective camouflage, concealment, and deception (CCD) techniques. Prior to US involvement in Vietnam, U.S. experience with the SA-2 was consistent with its use as a fixed strategic air defense system. The Soviets build the SA-2 as a road-mobile system, but never truly emphasized the mobility factor, and instead relied on fixed positions, arrayed in depth, to provide survivability and defend critical targets. The DRV, however, adapted a focus on mobility and CCD from the initial deployment of the SA-2 in-country.
The first SA-2 sites emplaced in the DRV were in a similar configuration to sites previously observed in the Soviet Union.[1] Sites were relatively easy to identify due to doctrinal Soviet site layouts- normally in a link configuration or a star-of-david pattern. Additionally, all of the key components of the SA-2 battalion were parked in revetments, which increased site survivability, but made for easier identification from the air.

Figure 5. DRV SA-2 site
Source: John Pratt, PROJECT CHECO REPORT: USAF Tactics Against NVN Air Ground Defenses December 1966-November 1968 (HQ PACAF, 1969), 3.
The North Vietnamese began a rapid program of site expansion throughout 1965. By October 1965 the intelligence community assessed the DRV had between 8-12 operational SA-2 battalions operating from over 30 sites.[2] By July 1966 the DRV had 25 SA-2 battalions in service.[3] This expansion trend continued throughout the Rolling Thunder campaign. At the time of the bombing halt in November 1968, the DRV had a total of 40 operational SA-2 battalions operating from 191 known sites.[4] Thus, for each operational SA-2 battalion, there were typically three to five prepared sites for them to operate from. Sites were typically within a few miles of each other, which allowed the DRV to adopt a "shoot and scoot" mode of operation from the very beginning, and greatly complicated the SAM targeting problem.[5] (See figure 5).
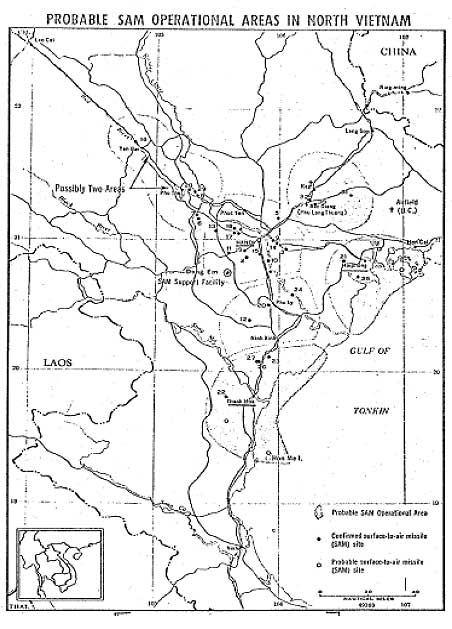
Figure 6. CIA Assessment of SAM operational areas, Fall 1965
Source: CIA, Soviet Military Personnel and Air Defense Operations in North Vietnam (Washington D.C.: 1965), 7.
Similarly, the DRV stressed the importance of mobility for its AAA force with roughly three to four prepared AAA sites for each battery above 37mm.[6] AAA sites were constructed rapidly, and the DRV demonstrated an ability to emplace a complete radar directed 85mm AAA site within six days.[7] As noted by an air-ground tactics report from 1969:
By mid-1968, the NVN defense network employed electronic equipment of "varying power/beam width/function/polarization/numbers/geographical distribution." Because it combined this resource with SAMs, AAA, and MiGs-- plus integration of the entire system--it was recognized as one of the most complex electromagnetic defense threats ever to be combated by USAF tactical forces. Effective enemy use of camouflage, mobility, and emission control compounded the problems, because good use was made of the equipment while minimizing the possibility of direct attack.[8]
The mobility factor was a primary survival mechanism for SA-2s operating in North Vietnam, but SA-2s also depended on mutual support from co-located AAA batteries. Realizing that SA-2s were vulnerable to low-altitude attacks, the DRV normally deployed four to eight gun 57mm batteries near SA-2 battalions. This provided a low- altitude point defense near the SA-2 site.[9] This point defense capability provided the North Vietnamese with a layered defense in depth that combined small arms, light, medium, and heavy AAA to cover the SA-2's "dead zone."[10] Further exacerbating the threat posed by AAA was the "Hanoi Habit," the name given by USAF F-105 pilots to the practice of every able bodied North Vietnamese peasant with a rifle or machine gun firing into the sky during air raids.[11]
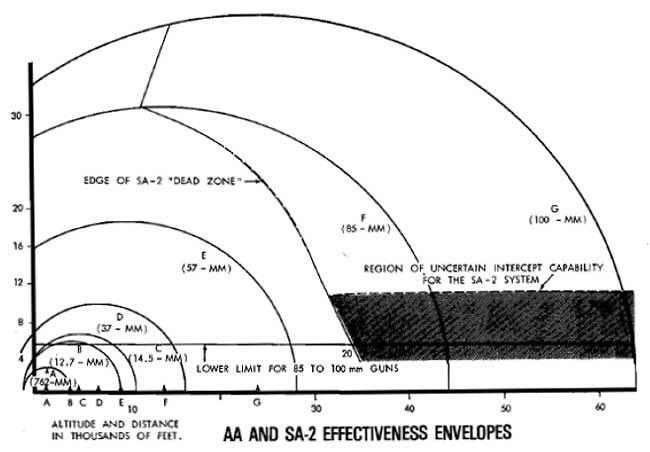
Figure 7. SA-2 and AAA layered defense
Source: Bernard Nalty, Tactics and Techniques of Electronic Warfare: Electronic Countermeasures in the air War Against North Vietnam 1965-1973 (Washington, DC: Office of Air Force History, 1977), 8.
Pacific Air Forces (PACAF) considered the North Vietnamese SA-2 mobility tactics the "primary reason for lack of success in attacking new sites." [12]Ultimately, the problem presented by the SA-2s in North Vietnam illustrated the fact that US reconnaissance systems, as they existed in August 1965, lacked the ability to provide timely and accurate intelligence on the DRV's defensive missile order of battle (DMOB).
Air Reconnaissance Capabilities and Limitations
Imagery Intelligence
At the time of the Leopard 02 shoot down, the USAF had a robust reconnaissance capability in place supporting air operations in Southeast Asia. In 1965 the primary air intelligence disciplines included visual reconnaissance, imagery intelligence (IMINT), and signals intelligence (SIGINT). Reconnaissance assets were split between 2nd Air Division/7th Air Force and Strategic Air Command (SAC). SAC assets generally supported national level intelligence tasking, and as such did not work directly for the 2nd Air Division or 7th Air Force commanders. Tactical reconnaissance assets were assigned directly to 2nd Air Division/7Air Force and supported both the "in country war" in South Vietnam, as well the "out country" war taking place in North Vietnam and Laos.[13]
IMINT disciplines consisted of photographic, infrared, and radar imagery. During Rolling Thunder, photographic imagery was utilized the most. Collection platforms included fighter tactical reconnaissance (TACRECCE), high altitude platforms, and drones. The primary tactical imagery platforms during Rolling Thunder included the RF- 101 Voodoo, and after July 1966, the RF-4C Phantom.[14] Both the Voodoo and the Phantom used a combination of oblique and panoramic cameras, and were primarily employed at low altitude, and operated under the code name Blue Tree.[14] In 1965, the primary high altitude imagery platform was SAC's U-2, which operated under the code name of Trojan Horse. A SAC Trojan Horse mission was responsible for the initial detection of the construction of the first SA-2 sites in North Vietnam on 5 April 1965.[16] In addition to manned imagery platforms, SAC also operated the Ryan Model 147B Lightning Bug reconnaissance drone. The Lightning Bug drones were launched by a DC-130 mother-ship, and later recovered by specially modified H-3 helicopters. The drone operations conducted against North Vietnam were conducted under the Blue Springs program.[18]
Each imagery platform had strengths and weaknesses as they related to collection against SAM sites. The U-2 provided wide area coverage, with medium resolution and was able to maintain standoff from known SAM sites. As the DRV increased their SAM coverage, the airspace over North Vietnam was denied to U-2 operations due to the SA- 2s previously demonstrated lethality against the U-2.[19] The RF-101 and RF-4C provided higher resolution imagery, but at the expense of increased threat exposure, and limited wide area surveillance capability. The Ryan drones offered high resolution imagery, with good survivability against the SA-2, but drone missions were complex to plan and execute.
The primary deficiency of all three platforms vis-a-vis the mobile SAM threat was the relatively long time required to process and exploit the imagery. Imagery was collected on wet film rolls, and had to be downloaded and exploited by imagery interpreters after landing. This required the collector to fly their route, return to base, download and then develop the mission film. After the film was developed, the photo- interpreters began to exploit the film, a process that could take minutes or hours depending on the target.
Under the Tactical Reconnaissance Intelligence System Enhancement (TAC RISE) system first introduced in June 1966, imagery exploitation requirements were subdivided into three phases.[20] Phase one, or initial phase, was for time critical reporting requirements. Initial phase imagery reports were textual reports (readouts) of targets that were sent via flash message from a wing communications center. Initial phase exploitation was the responsibility of the reconnaissance squadron that flew the mission, and was conducted in a mobile photo processing and interpretation facility (PPIF) facility typically located near the flight line. Phase two, or supplemental phase, was exploited at the Wing's reconnaissance technical squadron (RTS). The RTS was a mobile facility, and were the most manpower intensive imagery facilities utilized under the TAC RISE system, with 257 people assigned to each squadron. Supplemental phase reporting allowed mass production of imagery products, as well as additional textual reports for imagery customers. Phase three imagery reporting was conducted at a command reconnaissance intelligence technical squadron (RITS), and differed from first and second phase exploitation primarily due to the integration of all-source intelligence with the imagery, which was referred to as "reconnaissance intelligence."[21]
In August 1968 7th Air Force conducted a study to determine the timeliness of imagery intelligence support to USAF combat wings flying Rolling Thunder missions.[22] The study revealed that the average time from platform time over target (TOT) to initial phase imagery report (IPIR) production was 7 hrs 43 minutes, and on average it took 3840 hours for the IPIR to be received by the customer wing's communications center. Delivery of imagery prints averaged 39-51 hours via T-39 air courier.[23] This timeline demonstrates why imagery intelligence was less than useful for near real time targeting of mobile SAM sites. The huge time differential between collector TOT and usable imagery delivered to wings meant that the North Vietnamese had ample time to break down a SA-2 battalion and relocate to an alternate site.
Imagery derived intelligence was still vital to understanding how the DRV deployed and employed their SA-2 battalions, but not in a near-real time manner. Imagery intelligence provided value added by locating new SAM operating areas or sites, analyzing equipment and weapons for tactically significant changes, and building an overall understanding of the battlefield. In order to fix the problem of near real time geo- location of SAMs, the USAF would need to turn to signals intelligence.
Signals Intelligence
SIGINT consisted of two primary operational disciplines: communications intelligence (COMINT), the intercept and exploitation of communications signals; and electronic intelligence (ELINT), the intercept and exploitation of non-communications signals, primarily focused on radar transmissions. In addition to COMINT and ELINT, there is a third signals intelligence discipline: foreign signals instrumentation intelligence, or FISINT. FISINT deals with the interception of test telemetry to help reveal the capabilities of weapons systems. For purposes of this thesis, COMINT and ELINT will be the primary SIGINT focus. Like imagery platforms, SIGINT platforms throughout the USAF were split between SAC assets, including the RB-47H and RC-135, and tactical ELINT platforms including the RB-66B and C.
Historically, the SAC assets were used as standoff ELINT and COMINT collectors to develop an electronic order of battle (EOB) on a target country. SAC ELINT collectors flew throughout the Rolling Thunder campaign, but they typically operated on their own, and were not integrated into supporting strike packages. The RB-66 on the other hand was a tactical EW platform, and was capable of both ELINT collection as well as electronic attack (EA) against a target IADS, and was trained as a penetrating escort jammer if necessary. The RB-66 had two primary variants-- the EB-66C and the EB-66B. The EB-66C was primarily an ELINT collector, with some limited electronic attack capability. The EB-66C was primarily an EA platform, although it also retained some ELINT capability.[24] As early as December 1964 2nd Air Division submitted a requirement for a deployed ELINT capability in Southeast Asia. This request resulted in the initial deployment of RB-66Cs to Takhli AB, Thailand in May 1965.[25]
One of the primary advantages of ELINT over IMINT is that ELINT can be processed in near real time. The RB-66C mission crew consisted of four electronic warfare officers (EWOs) who operated the RB-66Cs receiver suite. This crew was able to monitor the signal environment in real time to develop an EOB and issue threat warnings to strike aircraft On 24 July, RB-66Cs detected SA-2 activity just prior to the shoot down of Leopard 02, but their SAM warning went unnoticed by Leopard flight who had temporarily stopped monitoring the threat warning frequency. The EB-66C provided timely ELINT warnings, but unfortunately due to system limitations, and a requirement to maintain standoff from high threat areas, they were unable to provide accurate geo- locational data on active SAM sites.
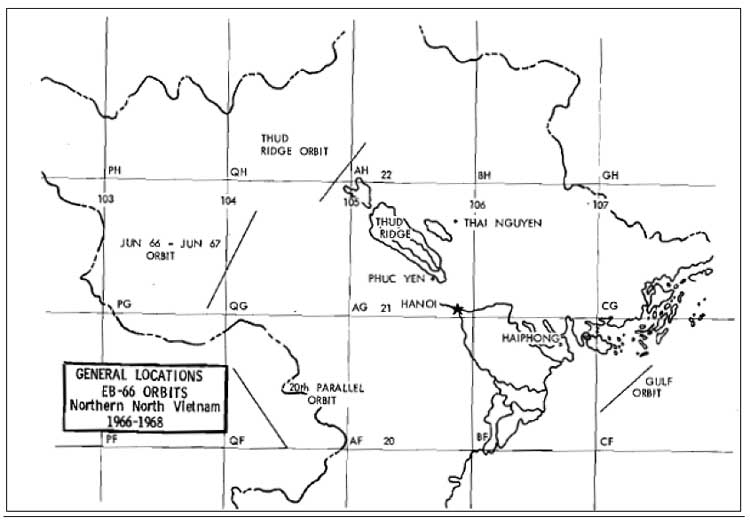
Figure 8. EB-66 Orbits during Operation Rolling Thunder
Source: Bernard Nalty, Tactics and Techniques of Electronic Warfare: Electronic Countermeasures in the air War Against North Vietnam 1965-1973 (Washington, DC: Office of Air Force History, 1977), 24.
Thus the USAF faced a dilemma. The primary imagery platforms were capable of finding SAM sites, but not fast enough to get inside the DRV's movement cycle and fix the SA-2 battalions on a near real time basis. The existing ELINT platforms were capable of providing near real time threat warning, but were incapable of accurately fixing the SA-2 battalions for strike aircraft to suppress or destroy. The USAF was facing a deadly adversary, lacked an effective countermeasure, and had begun to take unacceptable losses.
The Air Staff Task Force
The problem of how to counter the mobile SA-2 threat sent shockwaves through the Air Force. The Chief of Staff of the Air Force, General John P. McConnell, directed the Air Staff to convene an emergency working group to determine a way ahead to counter the unique challenges presented by the introduction of the SA-2, with associated DRV mobility tactics, into DRV. This led to the establishment of the Air Staff Task Force on Surface to Air Missiles in Southeast Asia chaired by Brigadier General Kenneth C. Dempster. Dempster served as the deputy director for operational requirements on the Air Staff. As deputy director for operational requirements, Dempster was in a unique position that allowed him to have excellent visibility into much of the classified research and development work that was occurring throughout the USAF and industry.[26]
The task force first met on 13 August 1965, a mere three weeks since the shoot down of Leopard 02 on 24 July. The task force convened for three weeks, and considered over 200 proposals from both the military as well as from industry and the scientific community.[27]
The key recommendations of the Air Staff Task Force were:
1. To modify a small number of fighters with electronic equipment to enable them to find active SAM sites. These aircraft would mark the active sites for destruction by accompanying Iron Hand strike aircraft.
2. To develop a missile that could be fired from a fighter and home on a radar emitter.
3. To develop jamming equipment for carriage on fighters to counter the SAM radars.
4. That a Radar Homing and Warning (RHAW) capability was needed immediately—a capability that would provide warning to the aircrews that a SAM radar was looking at them and provide some clue to its location.[28]
The first two recommendations led to the development of the first dedicated SAM suppression platform in the USAF inventory. This platform would be responsible for finding, fixing, and finishing SAMs in order to maintain freedom of movement for strike aircraft The second two recommendations led to the development of specialized defensive avionics that would improve fighter survivability in a dense SAM environment. Taken together, these recommendations would eventually allow US air forces to achieve parity with the DRV IADS by the time of the bombing pause in November 1968.
Wild Weasel I
In order to develop a fighter capable of finding and fixing the SA-2 sites, the Dempster task force began a rapid development program to develop, test, and train specialized "ferret" aircraft for this new role. The task force envisioned a two-seat fighter, equipped with mission specific avionics. The platform would be crewed by an experienced fighter pilot in the front seat, and an electronic warfare officer (EWO) operating the mission avionics in the back seat. The EWO would use the mission avionics to find and fix SAM sites in real time. The code name for this sensitive project was originally going to be Project Mongoose, but was quickly changed to Project Wild Weasel. The "Wild Weasel" [29] moniker still applies today to airframes and aircrew that fill the SAM suppression role.
In order to maximize understanding of the SA-2 threat, as well as potential U.S. counters to the SA-2, the USAF hosted an anti-SA-2 symposium in September 1965. This symposium was held at Eglin AFB, Florida, a location where the first Wild Weasel prototypes would undergo their initial developmental testing and evaluation. The anti-SA-2 symposium sought to achieve some synergy between the disparate intelligence and research and development efforts directed at the SA-2 Guideline system. This symposium included representatives from the USAF, the USN, the Department of Defense, as well as a myriad of government and intelligence agencies as well as industry representatives.[30]
Airframe Selection and Development The task force selected the North American F-100F Super Saber as the initial airframe to go through the Wild Weasel I modification. The F-100F was picked as the initial Wild Weasel aircraft primarily on the basis of availability. Due to the time critical nature of the Wild Weasel I development, testing, and fielding the ASTF needed to modify a number of aircraft quickly, and there happened to be multiple F-100Fs available. North American Aviation contractors prepared to do the initial aircraft modifications at the Air Logistics Command depot located in Sacramento, California. The F-100F was envisioned as a transition airframe. The F-100F would later prove to be a poor fit for the Wild Weasel mission, as its operating airspeed was not compatible with the much faster F-105s and F-4s that constituted the strike aircraft force operating in Southeast Asia.[31]
Central to the development of the Wild Weasel I airframe was the development of a radar homing and warning set and other specialized avionics. The USAF was not unfamiliar with the concept of a radar homing and warning receiver. Ironically, in the spring of 1965 the USAF had turned down a proposal from the Bendix Corporation for the installment of a RHAW system in the F-100. This proposal had been turned down because "there was no requirement for it."[32] Now, less than six months later, the Air Staff turned to the ATI Corporation in Palo Alto, California. ATI was known to the Air Staff Task Force members due to their development of avionics for "black" programs, such as the System XII RHAW fielded on the U-2.[33]
ATI sent representatives to brief the Task Force on their proposal for an improved RHAW, called the Vector system. At the time of the proposal, the Vector system existed only as a concept sketch. The task force decided that the Vector system would be the baseline RHAW for the Wild Weasel program, and eventually the Vector RHAW would be installed in all tactical fighters to provide timely warning radar threat systems. ATI was awarded the contract for the development for the Vector, and was tasked with a 30 day requirement for production of the initial sets. This aggressive timeline--30 days from concept to hardware ready for installation--was indicative of the time critical nature of the development of Wild Weasel I. In addition to the Vector RHAW system, ATI also proposed the development of two additional avionics systems for integration into the Wild Weasel I aircraft. These systems included the IR-133 panoramic scan receiver, and the WR-300 launch warning receiver (LWR). Like the Vector system, the IR-133 and the LWR were all concept sketches at the time of the initial task force briefings, but ATI managed to produce systems within a month of receiving the contract. The Wild Weasel I aircraft were modified and went through initial equipment testing in October 1965.[35]
The Vector RHAW was a passive receiver that was used to provide warning of threat radar activity. The Vector system operated in the C, S, and X-Bands and provided the crew a direction and relative intensity for threat radars. The direction was provided by an azimuth strobe radiating from the center of the display, and the intensity was depicted by a set of concentric rings. As a threat system got closer, the intensity would increase and the strobe would extend further outward on the scope. Crews could differentiate between C, S, and X-Band signals by the appearance of the strobe, which was solid, dashed, or dotted depending on which band the threat operated in.[35]
The second system developed by ATI was the IR-133 panoramic scan receiver. The IR-133 allowed the EWO to analyze threat signals and determine relative signal strength on either side of the aircraft By observing the signal strength differential on either side, the EWO could work with the pilot to zero out the difference, and point the Weasel aircraft towards the active site in order to attempt a visual identification of the site.[36]
The third system developed and fielded in Wild Weasel I was the Launch Warning Receiver. The LWR looked for the missile guidance uplink that was transmitted from the Fan Song upon missile launch. This uplink served to both interrogate the missile beacon, as well as to transmit guidance commands to the missile. The missile guidance uplink operated in L-Band, and when noted by the LWR, provided the EWO warning that a missile was on its way. This allowed the Wild Weasel to monitor FAN SONG activity and provide warning to the strike force in real time when a launch occurred.[37]
The last system developed for the Wild Weasel I was the SEE-SAMs (See, Exploit, and Evade SAMs) system. SEE-SAMs allowed the EWO to determine if the aircraft was located in the center of the Fan Song's track-while-scan scan volume. Additionally, SEE-SAMs monitored the pulse repetition frequency (PRF) of the Fan Song to help warn of impending launch. Doctrinally, an SA-2 site operated in low pulse repetition frequency while it was acquiring and initially tracking a target. As the SA-2 site prepared to launch, the Fan Song would be switched into a high PRF mode, which allowed for faster updates on the target. The SEE-SAMSs provided an audible tone, as well as a flashing "Azimuth Sector (AS)" light to warn the crew that a missile launch was imminent.[38]
Crew Training and Tactics Development
While the Wild Weasel I aircraft were being modified, the initial Wild Weasel cadre were selected. The Wild Weasel I project initially consisted of three crews, and two modified F-100Fs. This plan was rapidly expanded to include a total of 5 crews, and four modified F-100F Wild Weasel aircraft. The crews consisted of experienced F-100 pilots, along with hand selected EWOs. All crew members were volunteers. The selection of EWOs was particularly interesting, and demonstrated the USAF's willingness to break some traditional paradigms in rapidly developing and fielding Wild Weasel I. Unlike the pilots selected for the Wild Weasel I program, who were all highly experienced in fighters, the EWOs all came from the bomber (B-52, B-58) or electronic warfare (EB-66) communities. Due to the tight security associated with the Wild Weasel program, the pilots and EWOs were not clear what program they were volunteering for. Upon being notified of their proposed mission, one of the EWOs responded incredulously with, "You gotta' be shittin' me." "YGBSM" then became the unofficial Wild Weasel motto.[40]
The initial tactics and training phase took place on the ranges around Eglin Air Force Base, Florida. This phase ran from 1 November 1965 until the first Wild Weasel detachment deployed on Thanksgiving Day, 21 November 1965. Eglin was a facility accustomed to sensitive testing and planning projects which allowed the Wild Weasel detachment to conduct their training in relative secrecy. Additionally, Eglin maintained one of the only training replica SA-2s in the US inventory. This emitter, called Soviet Air Defense System-1 (SADS 1) was the primary radar sources used for testing and training the initial Weasel tactics. The testing and training period at Eglin was necessary for both familiarization with the new systems in the Wild Weasel I platform, as well as for initial tactics development prior to deploying to Southeast Asia.[41]
Crew coordination in the F-100F was a critical mission concept that needed work during the Eglin phase. Pilots selected for the Wild Weasel I program were all single seat fighter pilots, with no previous experience flying multi-seat airplanes. The EWOs were all from multi-crew airplanes. This difference in background required the pilots and EWOs to learn to work together as a team in the F-100F. Pilots and EWOs were allowed to informally self-pair as combat crews, and with minor exceptions, they became "hard crewed" together for the duration of training and combat deployment. This allowed for improved superior coordination and combat employment.[42]
Throughout the fast paced testing and tactics phase at Eglin, the crews developed the initial tactics the crews planned on using in combat in SEA. The normal tactic consisted of an initial signal acquisition, using the Vector system, followed by the crew conducting a homing run against the threat emitter. As the aircraft approached the emitter, the EWO would transition from the Vector system to the IR-133 panoramic receiver to provide fine-grain course corrections to enable the Weasel aircraft to approach the SAM site. The tactic required the crew to then transition from an electronic search to a visual acquisition of the emitter site. Crews were trained to look for the tall tale signature of "station passage," when the F-100F overflew the emitter site. This allowed them to refine their visual search in order to identify the target emitter.[43]
Training with the SADS-1 emitter on the Eglin ranges presented some inherent problems that decreased the effectiveness of the training on the Eglin complex. First, the terrain around Eglin AFB was extremely flat. This was in stark contrast to the mountainous terrain approaching the Red River Valley of North Vietnam. This limited the training program from replicating low altitude tactics as they would be conducted over the DRV. Secondly, the SADS-1 emitter was a fixed site, and relatively easy to identify from the air. This decreased realism, and did not account for the excellent camouflage and mobility tactics employed by the DRV's SAM battalions. With these limitations in mind, the USAF decided to deploy the Wild Weasel I detachment to Southeast Asia for a combat operational test and evaluation period.
Combat Evaluation
The crews and aircraft deployed on 21 November 1965, and arrived at Korat Royal Thai Air Base, home of the 388th Fighter Wing. The initial combat deployment to Southeast Asia was intended as a combat operational test and evaluation. The objectives set for the combat deployment were:
1) To determine the warning capability of RHAW equipment installed in the Wild Weasel F-I00F aircraft
2) To investigate the effect of jamming by friendly aircraft on Vector and IR-133 equipment
3) To determine the homing accuracy of the RHAW equipment and the capability of the crew to place the aircraft within visual range of the target.
4) To develop tactics for employing the Wild Weasel aircraft against SAM systems.
5) To determine maintenance requirements and reliability of RHAW equipment
6) To determine the organizational and manning requirements for Wild Weasel operations
7) To determine training requirements for flight crews and RHAW maintenance personnel
8) To test any additional equipment which may be made available for this system during the period of operational test and evaluation.[44]
Upon arriving at Korat Air Base, the Wild Weasel Detachment attended a number of briefings with 388th Fighter Wing personnel in order to introduce themselves, and to introduce their proposed tactics. On 28 November, the Weasels began flying their first orientation sorties. During the orientation sorties, the F-100Fs would fly along the DRV's border, and rendezvous with an EB-66. Both platforms would monitor the signal environment, and coordinate in real time to confirm that the Weasel's avionics were operating properly. Following the orientation sorties, the Weasel detachment flew their first combat sortie over North Vietnam on 1 December 1965.[45]
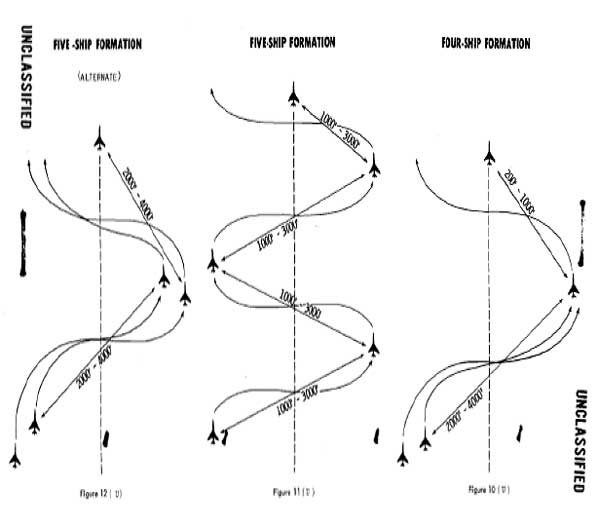
Figure 9. Initial Iron Hand Formations during Wild Weasel I
Source: Nalty, Tactics and Techniques of Electronic Warfare: Electronic Countermeasures in the air War Against North Vietnam 1965-1973 (Washington, D.C.: Office of Air Force History, 1977), 39.
The initial tactics developed by the Weasels consisted of the F-100F acting as a pathfinder for a three or four-ship of F-100Ds. The F-100F would detect and home on any active SAM sites, and then mark the site for the F-105Ds, who were employing as the "killer" element of the Wild Weasel hunter-killer team. In order to perform this role, the F-100Fs were loaded two pods of 2.75 inch high velocity aerial rockets. The F-105D ordnance varied, but could include gravity bombs, napalm canisters, or rockets.
The first few weeks of Weasel operations allowed the crews to develop and validate tactics, but resulted in no successful kills on SA-2 sites. The Weasel detachment typically flew two sorties per day. On 20 December 1965, the Wild Weasel Task Force suffered its first combat loss, when an F-100F was shot down by AAA while leading an unsuccessful attack on a SAM site near Kep airfield. The shoot-down resulted in the pilot, Capt John Pritchford, being captured and the EWO, Capt Robert Trier, being killed in action.[46]
Two days later the Wild Weasel detachment was able to avenge its loss when it achieved its first SAM kill of the war. Leading a Rolling Thunder strike against the Yen Bai rail yard, the Weasel, using the call-sign Spruce 01, began a low altitude homing run on an active SA-2 site. Using terrain masking tactics during their approach to the SA-2, Spruce 01would update their fix on the SAM each time they "unmasked" over a ridgeline. As Spruce flight crossed the last ridgeline and entered the flats of the Red River Valley, they were able to visually acquire the SA-2 battery. The Fan Song radar was located in the center of a village, and missiles were noted partially hidden under a thatched hut. The entire site was well camouflaged, and difficult to identify from the air. Spruce 01 launched rockets into the site, and then followed up with a strafing run using their 20mm cannon. Spruce 01 observed that the Fan Song emissions ceased, indicating that the battery had been suppressed. The accompanying F-105Ds were able to acquire the site due to Spruce 01's mark, and commenced their attack.[47] The attack was a complete success, and resulted in the total destruction of the SAM site. The Wild Weasel concept had been validated. Only 151 days had passed since the shoot-down of Leopard 02.
Following the first SAM kill on 22 December, the Weasel detachment continued to adjust and refine their tactics against the North Vietnamese IADS. The formal end of the operational test and evaluation was 26 January 1966, but the Weasel detachment remained in place at Korat AB flying combat missions.[48]
Wild Weasel II and III
The initial test and evaluation identified the F-100F as a poor airframe choice for the Wild Weasel airframe. Airspeed limitations on the F-100F made it difficult to operate with the faster F-105s and F-4s that were the primary strike and escort aircraft operating over the DRV. Thus one of the first results of the F-100F combat test and evaluation was the development of an F-105 based Wild Weasel platform.
Airframe Development
The initial attempt at developing an F-105 based Wild Weasel platform was called Wild Weasel II. It consisted of a modified F-105F, two-seater, with the homing avionics located in wingtip pods. This variant was quickly scrapped after flight tests revealed that the pod based systems caused excessive vibration limiting the aircraft's maximum speed. Wild Weasel III was the next iteration, and consisted of an F-105F fitted with the same internal avionics used on the F-100F Wild Weasel I program.[49]
Wild Weasel College
In addition to developing a replacement airframe for the F-100F, the USAF recognized a need to capture the tactical expertise developed by the initial Wild Weasel I crews. Some of the initial Wild Weasel I cadre were assigned to Nellis AFB, Nevada to create the Wild Weasel College. The Wild Weasel college existed to train new Weasel aircrews immediately prior to their deployments to Southeast Asia. Nellis AFB, with its massive range complex, provided an ideal site for training. In addition to the Wild Weasel College, Nellis was home to the USAF Fighter Weapons School. The Weapons School conducted the USAF's most demanding tactics courses for select aircrew. This allowed the Wild Weasel college to integrate their training missions with other airframes operated at the USAF Weapons School.[50]
Shrike and Standard ARM
A third result of the Wild Weasel I test and evaluation was the fielding of the AGM-45 Shrike missile on Wild Weasel platforms. The original tactics developed by the F-100F required the Weasel aircraft to electronically home on the FAN SONG signal, and then transition to a visual lookout as they approached the missile site. Once the crew was able to visually identify the site, they were required to close with the site in order to attack it with rockets or 20mm cannon fire. Similarly, accompanying F-105Ds had to close with the site to attack with similar weapons, or with canisters of cluster bombs or napalm canisters. In any case, the Iron Hand flights were suffering losses, primarily due to the co-located AAA batteries that operated in coordination with North Vietnamese SA- 2 sites. In order to reduce risk to Iron Hand flights, and provide a more effective suppression capability the USAF sought to develop an anti-radiation missile (ARM) that would enable the Weasel aircraft to engage SAM sites from extended ranges. The ARM requirement had been identified by the Air Staff Task Force, and combat operations during the Wild Weasel I deployment had validated that requirement.
Fortunately, the United States Navy had already developed a passive homing anti- radiation missile designated the AGM-45 Shrike. The Shrike was an 800 pound missile, equipped with a radar proximity fused 140 pound warhead. The Shrike had a passive radio frequency receiver in the nose which allowed it to home on any active radars.[51] The Shrike's range was approximately eight nautical miles, but if "lofted" by the launching aircraft the Shrike could reach out to approximately twelve nautical miles.[52] The Shrike's primary disadvantages were its range, which was less than the SA-2's max effective range of 17 nautical miles; and the fact that if the target radar shut down during the Shrike's time of flight, the missile would cease guiding and miss the target. The AGM-45 was quickly deployed to Southeast Asia, and the initial use of the AGM-45 in combat was on 18 April 1966 when an F-100F engaged a AAA fire control radar.[53] The Shrike quickly caused the North Vietnamese to modify their tactics:
Since the Shrike's introduction, the percentage of SAMs fired with radar guidance has been greatly reduced. The far greater number are fired in salvo and are unguided because the ground sites cannot afford to stay on the air. This has greatly reduced their effectiveness and has been a big boost to the morale of the strike pilots. It should surprise no one that an increase in SAM firings and an increase in Shrike firings occur at the same time. Most Shrike launches are the result of SAM activity and launch warnings.[54]
Despite the successes of the Shrike in combat, crews identified a requirement for a longer range missile that allowed them to maintain greater standoff from active SA-2 sites. This requirement, first captured in 1967, led to the joint USAF/USN acquisition of the General Dynamics AGM-78 Standard Anti-Radiation Missile (STARM) in early 1968. The STARM was a massive missile--1370 pounds, with a 215 pound warhead--and provided Weasel aircrew with a range of almost 40 nautical miles. Subsequent modifications to the AGM-78 included a red-phosphorous warhead marker, which made visual acquisition of missile impacts easier, and allowed Weasel hunter killer teams to visually acquire engaged Fan Song radars, and prosecute additional attacks in order to "mop up" sites via gravity bomb attacks.[55]
Wild Weasel III Combat Operations
In May 1966 the first F-105F Wild Weasel III aircraft arrived in Southeast Asia to begin their inaugural combat deployment. F-105Fs were deployed to both F-105 wings in Thailand- the 388th Fighter Wing at Korat AB, and the 355th Fighter Wing at Takhli AB. The Weasel aircraft were organized differently at each wing. At Korat AB, all F-105Fs were assigned to a single Wild Weasel squadron. This squadron would then support strike packages from the other fighter squadrons assigned to the 355th FW. At Takhli, the Weasel aircraft were divided up between the Wing's fighter squadrons. The Weasel aircraft then became a flight within each fighter squadron.
As the F-105Fs refined their tactics against the North Vietnamese IADS, two distinct types of missions evolved. The original hunter-killer mission, referred to as Wild Weasel missions, consisted of F-100Fs or F-105Fs working with F-105Ds to seek out SA-2 sites. The intent of these missions was to locate and destroy any SA-2 sites that happened to come on-air. In the parlance of F3EA, the Wild Weasel missions sought to find, fix and finish SAMs, with the "finish" resulting in destruction of SAM battery. Hunter-killer missions were typically conducted independent of other strike operations occurring throughout the DRV. With the introduction of the AGM-45, the mission focus began to shift. Now, Wild Weasel aircraft were used primarily in an Iron hand role. The Iron hand role used the Weasel aircraft to support larger Rolling Thunder strike packages. Throughout 1966 the Iron Hand missions evolved into more of a suppression role. The Wild Weasels would serve to provide warning and suppression of any threats along the strike route that were a factor. Additionally, Iron Hand flights would troll for SAMs in an attempt to force the DRV IADS to focus their targeting efforts on them, vice the strike aircraft[56] This subtle shift is would best described as find, fix, and finish SAMs, with the "finish" resulting in temporary suppression of SAMs in order to allow the strike package to operate unmolested by the SAM threat. A 7th Air Force tactics conference noted that by the end of 1967:
. . . a clear difference between the WILD WEASEL and the IRON HAND missions. WILD WEASEL consists of an electronic and visual search for SAM positions and the destruction of those positions and associated hardware. IRON HAND consists of providing an electronically guarded corridor through which the strike force can pass with the warning capability and protection (strike threat) provided by the F-105/F/D. The IRON HAND mission is primary of the two under our present method of operation.[57]
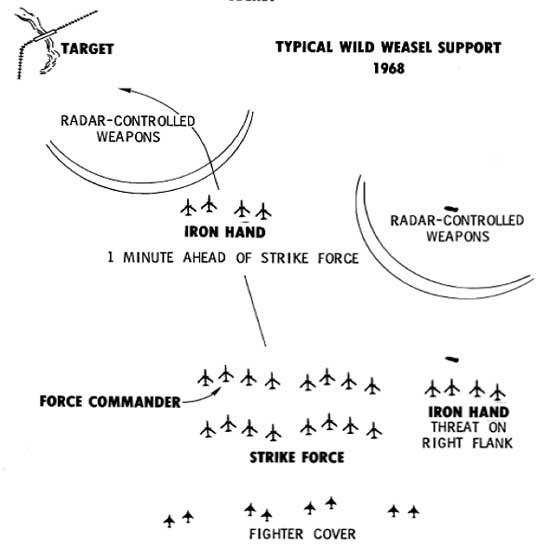
Figure 10. Iron Hand / Strike Package Integration
Source: Nalty, Tactics and Techniques of Electronic Warfare: Electronic Coantermeasares in the air War Against North Vietnam 1965-1973 (Washington, D.C. Office of Air Force History, 1977), 47.
The concept of suppression resulted from the tactical choices provided to North Vietnamese air defenders. Once the AGM-45 was provided targeting information by the EWO, and launched at an active Fan Song, the AGM-45 was capable of autonomously homing in on the radar. If the radar continued to emit, and remained "on air," the AGM-45 had a high probability of impacting the radar and damaging the antenna and other components. If the Fan Song operators detected an AGM-45 launch, they had the option to continue the engagement, while running the risk of taking a hit from the inbound AGM-45, or the Fan Song could cease transmitting. If the Fan Song ceased transmitting, the missile battery would lose control of all missiles in flight, and the missiles would go ballistic. In either case, the Weasel crew created a suppression effect- whether by kinetic impact, or by forcing the North Vietnamese to cease radiating.
Action and reaction
The North Vietnamese reaction to the emerging SAM suppression capability was based on continued mobility and CCD improvements as well as strict adherence to emission control procedures as enabled by increased integration throughout the North Vietnamese IADS.
The North Vietnamese realized the significant threat posed by SAM suppression operations. Merle Pribbenow, a retired Central Intelligence Agency case officer and Vietnamese linguist noted:
"The impact of these attacks on the missile crews was devastating. Unlike most North Vietnamese soldiers, the crews were largely well-educated urban youth unaccustomed to hardship, whose training had concentrated on technical skills rather than combat and ideology. Entire missile units wavered, afraid to fire a missile for fear a launch would expose them to attack. In 1966 a senior Air Defense Command officer observing combat operations with a missile battalion near Haiphong, was so frustrated by the reluctance of the battalion commander (who claimed U.S. jamming made it impossible to identify a target) to fire on U.S. aircraft that he finally exploded in anger. "Even my old eyes can see the target on the screen," he shouted at the young officer. "Launch your missiles, damn it! They're attacking the Uong Bi power plant!."[58]
The North Vietnamese Air Defense Command was a learning organization, and sought to spread successful tactics from battalion to battalion. The Air Defense Command would hold tactics conferences in order to examine successful tactics and countermeasures.[59] This process allowed the North Vietnamese IADS to adapt in response to U.S. innovations in aerial combat- whether Wild Weasels, anti-radiation missiles, or electronic-countermeasures. The North Vietnamese focus on improved mobility was an example of a North Vietnamese counter to a U.S. tactical innovation.
In order to increase mobility, the North Vietnamese adapted the concept of a "short battalion." This name, given by U.S. photo-interpreters, described non-doctrinal batteries utilizing only three or four Guideline launchers, vice the doctrinal six Guideline launchers. This provided the missile crews with marginally decreased firepower, with a commensurate increase in their ability to rapidly shoot and scoot.[60] Likewise, during 1965, and 1966, intelligence analysis noted a trend towards SAM engagements in the afternoon or at night. This provided the missile crews an opportunity to engage with an option to relocate under the cover of dusk or darkness in order to be at a new site in the morning.[61] Additionally, once occupying a new site, SA-2 crews were trained not to emit until actually conducting an engagement. This emission control tactic allowed the crews to maintain some tactical surprise when operating from a newly occupied site.[62]
The threat of detection by Wild Weasel platforms, and specifically the threat posed by anti-radiation missiles including the Shrike and Standard-ARM led the North Vietnamese to put an increased emphasis on emissions control during engagements. Prior to the introduction of a SAM suppression force, North Vietnamese SAM batteries would consistently radiate for extended periods as they worked through the SAM battery's "kill chain" from acquisition to track to engagement. Emission periods of up to five minutes were commonplace.[63] As the lethal threat to SA-2s increased, the SAM batteries became much more so reliant on their integration into the overall IADS. The North Vietnamese IADS was capable of establishing accurate tracks of inbound strike aircraft and sending those tracks down echelon to the SAM batteries. This allowed the SAM batteries to passively monitor inbound strike packages via tracks provided from the IADS, as well as via local early warning/acquisition radar performing direct support for the SAM battery. The result was that the SA-2 crew could plot inbound tracks, and pre-position their radar scan volume around the expected track location, and then proceed to radiate, track, and engage. This process allowed the SA-2 operators to decrease their emission times to less than thirty seconds from initial emission to engagement.[64]
Developing an Understanding of the Threat
The Rolling Thunder campaign saw some revolutionary changes with respect to weapons employed by both sides during 1965, and the first half of 1966. The introduction of the SA-2 to the North Vietnamese IADS was countered by the introduction of dedicated Wild Weasel platforms, armed with anti-radiation missiles. Other revolutionary changes, although outside the scope of this thesis, are worth mentioning. The fielding of electronic-countermeasures (ECM) pods on the majority of USAF platforms caused a significant shift in both US and North Vietnamese tactics. Advances in electronic identification allowed air to air platforms, specifically F-4s, to identify North Vietnamese MIGs at significant ranges. Interspersed throughout these major "revolutionary" changes, the U.S. and DRV continued a tactical cat-and-mouse game with smaller evolutionary tactical changes to gain the upper hand in the air war over North Vietnam. The Air Force's ability to adapt to these tactical changes was only as good as its understanding of the North Vietnamese IADS capabilities and tactics. This understanding is gained through the "exploit and analyze" phases of the F3EA cycle, which will be described in the next chapter.
[1]Staaveren, 161.
[2]Central Intelligence Agency, 1965, 1.
[3]Burch, 22.
[4]Monte D. Wright, PROJECT CHECO REPORT: USAF Tactics Against Air & Ground Defenses in SEA November 1968-May 1970 (HQ PACAF, 1970), 177.
[5]Central Intelligence Agency, 2.
[6]Pratt, 2.
[7]Burch, 19.
[8]Pratt, 16.
[9]Nalty, 8.
[10]Ibid.
[11]Pratt, 2.
[12]Melyan and Bonetti, 5.
[13]William C. Thorndale, PROJECT CHECO REPORT: Tactical Recon Photography Request/Distribution (HQ PACAF, 1969), 17.
[14]Edward P. Brynn, PROJECT CHECO REPORT: Reconnaissance in SEASIA JUL 1966-JUN1969 (HQ PACAF, 1969), 43.
[15]5Brynn, 28.
[16]Earl H. Tilford, Setup: What the Air Force Did in Vietnam and Why (Maxwell AFB AL: Air University Press, 1991), 113.
[17]Paul W. Elder, PROJECT CHECO REPORT: Buffalo Hunter, 1970-1972 (HQ PACAF, 1973), 10.
[18]Mark E. Smith, PROJECT CHECO REPORT: USAF Reconnaissance in Southeast Asia (1961-1966) (HQ PACAF, 1966), 34.
[19]Elder, 1.
[20]Thorndale, 4.
[21]Ibid.
[22]Thorndale, 46.
[23]Ibid., 47-48.
[24]Nalty, 17-19.
[25]Brynn, 73.
[26]Price, 47.
[27] Edward T. Rock, First In Last Out: Stories by the Wild Weasels (Bloomington, IN: Authorhouse Books, 2005), 6.
[28]William A. Hewitt, "Planting the Seeds of SEAD: The Wild Weasel in Vietnam" (Masters Thesis, Air University, School of Advanced Airpower Studies, 1992), 12.
[29]Rock, 9.
[30] Price, The History of Electronic Warfare Volume III (The Associaton of Old Crows), 47-48.
[31]Rock, 9.
[32]Ibid., 6.
[33]Price, 44.
[34]Rock, 44.
[35]Davis, 8-10.
[36]Rock, 9-10.
[37]Nalty, 34.
[38]Price, 73.
[39]Allen Lamb, "The First Wild Weasel and the First Wild Weasel SAM Kill" In First In, Last Out: Stories by the Wild Weasels (Bloomington IN: Authorhouse Press, 2005), 88.
[40]Ibid., 89.
[41]Nalty, 84.
[42]Davis, 10.
[43]Nalty, 35.
[44]Rock, 11.
[45]Ibid., 142.
[46]Davis, 12.
[47]Rock, 93-94.
[48]Nalty, 40.
[49]Ibid., 40-41.
[50]Thornborough, 55-57.
[5]Nalty, 42.
[52]Price, 70.
[53]Ibid., 71.
[54]Pratt, 32.
[55]Thornborough, 69-70.
[56]Pratt, 29.
[57]Ibid..
[58]Pribbenow, 178.
[59]Ibid., 193.
[60]Melyan and Bonetti, 103.
[61]Ibid., 104.
[62]Ibid.
[63]Price, 94.
[64]Ibid., 95.
CHAPTER 4 Exploitation and Analysis
Introduction
The intent of this chapter is to examine how USAF SAM suppression forces used intelligence exploitation and analysis to allow them to find, fix, and finish SAMs. Additionally, this chapter seeks to describe how exploitation and analysis of intelligence provided an enhanced understanding of the North Vietnamese IADS. This understanding allowed USAF forces to improve their electronic combat systems and weapons. Additionally, this understanding helped aircrew refine tactics, techniques, and procedures allowing them to operate effectively in the high threat route packs of North Vietnam.
Types of Intelligence In order to further develop the exploitation and analysis effort, two terms must be defined. For purposes of this chapter, two types of intelligence reporting will be referenced. "Intelligence reporting" refers to intelligence collected by traditional intelligence collection platforms, and produced by intelligence production organizations. As discussed in chapter three, the traditional intelligence disciplines used most during Operation Rolling Thunder were imagery intelligence as well as the two primary sub- disciplines of signals intelligence (communications intelligence and electronic intelligence). Intelligence reporting is reported via standardized intelligence formats including serialized reports and annotated imagery products. Intelligence reporting varied from raw single-source reports to comprehensive all-source assessments.
A second type of intelligence reporting will be referred to as "aircrew derived intelligence." Aircrew derived intelligence refers to the collection, analysis, and reporting of intelligence information gleaned from combat missions flown by platforms not traditionally associated with intelligence collection. For purposes of this thesis, this includes aircrew reporting from any USAF aircraft that penetrated the airspace of North Vietnam. Aircrew derived intelligence is a critical component to any all-source intelligence analysis as it results from the direct interaction with the threat IADS and its associated weapons systems. This intelligence is captured as the IADS is in the process of carrying out its mission of airspace defense, and as such gives a unique perspective critical to understanding the threat network that is an IADS.
Aircrew derived intelligence is produced by the traditional combat intelligence debriefing and reporting cycle that has existed since World War I. At the fighter wing level, four essential intelligence requirements existed:
1. What are the threats, and where are they? (Threat order of battle)
2. What are the threat system capabilities and vulnerabilities? (Threat System Capabilities)
3. How are the North Vietnamese employing their threat systems? (Threat Tactics)
4. How are threats integrated into the North Vietnamese IADS? (Threat Integration)
The Operations Cycle—Rolling Thunder
The operations cycle during Operation Rolling Thunder was centered on the planning, execution, and recovery of Alpha strikes. Each day 7th Air Force issued a tasking order to the flying wings throughout Southeast Asia. This tasking included a typical requirement of two Alpha strikes per day per wing, plus additional taskings supporting air operations in Laos, or in the lower threat route packs of North Vietnam. The Wild Weasel detachments, co-located with the strike wings located at Takhli AB and Korat AB primarily supported Alpha strikes, but also provided support to other taskings as dictated by the threat level.[1]
Taskings were issued daily to the wings and were transmitted as part of the daily "frag," or fragmentary order. This order was produced by planners at 7th Air Force headquarters. The frag specified which targets were to be hit, what assets were tasked to take part in the strike, and provided coordinating information. Additionally, the frag provided restrictions and constraints. This message was encrypted and transmitted to each wing's communications center. Frags typically arrived in the late afternoon. When the frag was received, the mission planners began the process of "breaking out" the frag. For each fragged mission, the wing leadership would select a mission commander. The mission commander was the aircrew member that was in overall charge of the planning, execution and debriefing effort in support of each alpha strike.[2]
Under the leadership of the mission commander, the mission planning team began the detailed planning necessary to launch a large Alpha strike against North Vietnam. Aircrew were provided to the mission planning effort by the subordinate flying squadrons within the wing. The aircrew began assembling and annotating maps as well as producing flight lineup and navigation cards, which would be used to execute the strike the following day.[3]
Supporting the planning effort was the wing's intelligence section. The intelligence section searched their archives for applicable maps and target imagery to enable the strike mission. Additionally, the intelligence section reviews the results of previous strikes against, or near, the fragged target area with the intent of predicting the enemy defenses as accurately as possible.[4] In order to predict the expected enemy defenses, the intelligence shop assessed the disposition of enemy forces, referred to as "order of battle." The order of battle consisted of four primary focus areas—electronic order of battle, SAM order of battle, air order of battle, and AAA order of battle. In addition to the order of battle, the intelligence shop assessed the likely tactics used by the North Vietnamese IADS. This understanding of the North Vietnamese IADS was integrated into the planning effort throughout the entire planning cycle.
The next step in the operations cycle was the pre-mission mass brief. This briefing typically started two hours prior to engine start time and included all the Wing's flights fragged to fly on the mission. This typically included strike aircraft and Wild Weasel flights. Additionally, based on recommendations made at each F-105 wing, by 1967 the wings had integrated support platforms into the mass briefings--including EB-66 Destroyer and KC-135 tankers--which improved teamwork and helped mission effectiveness.[5]
The mass brief provided a weather update, a common threat picture, and then covered the planned mission in detail. Following the mass brief, each flight or element would proceed to their respective squadron areas for a more detailed flight briefing, after which the aircrew would don their survival gear, and proceed to launch the strike. Once the strike force was launched, the wing would monitor the operation via radio. Following the mission, the strike force would recover at their home stations, and begin the debriefing process.
The debriefing process consisted of four main debriefs- maintenance debrief, intelligence debriefing, mass debriefing, and flight debriefing. The maintenance debrief was conducted to inform the maintainers of any maintenance issues that occurred during the mission. Following maintenance debrief, the aircrew would proceed to the wing operations center for their intelligence debriefing. Intelligence debriefing was conducted by a team of intelligence debriefers. The debriefings were focused on mission results, enemy target information, observed enemy tactics, techniques, and procedures, and on any significant events that occurred during the mission. The results of the intelligence debrief were typed up in an operations report (OPREP) message that summarized both the results of the mission, as well as observed enemy reaction and tactics. The OPREP was sent via the wing communications center, and was sent both laterally to other wings, as well as up-echelon to 7th Air Force. The OPREP served as a permanent record of the mission, and was used by both operations and intelligence for building their understanding of the North Vietnamese IADS.[6] Following intelligence debrief, the aircrew then conducted a mass debrief. The intent of the mass debrief was to capture lesson learned from the mission.
From the beginning of the Wild Weasel program, the aircraft were modified to allow them to critical mission data in order to facilitate the debriefing process and the capture of aircrew derived intelligence. Specifically, both Wild Weasel I and Wild Weasel II airframes were built with the KA-60 strike camera. The KA-60 strike camera was used to assess effectiveness of weapons employment, as well as to provide a visual record of targets and significant events in the target area. Additionally, the Wild Weasel aircraft were modified with a multi-channel audio recorder. This recorder allowed the recording of intercom communications between the pilot and EWO, external communications from aircraft radios, and audio created by the Wild Weasel mission avionics. This provided the crew a limited ability to reconstruct tactically significant events in during the debriefing process. This was a vital source of aircrew derived intelligence, and helped refine Weasel tactics, techniques, and procedures.[7]
At the end of each mission, the aircrew would annotate mission highlights and lessons learned in a mission log book. This book served as a central repository for accumulated knowledge, and was reference early and often in the planning process. The operations cycle was completed when the flight debriefing was over, OPREPs were submitted to 7th Air Force, and the wings began their preparation for the next day's missions.[8]
Understanding Threat Disposition
A primary effort at the wing level was the maintenance of threat situation displays annotated with the most current order of battle. This was a continuous effort that combined formal intelligence reporting as well as aircrew derived intelligence. Although threat displays varied somewhat from wing to wing, the threat display from Takhli's 355th Fighter Wing in 1967 is typical. The central threat display consisted of a large scale map and imagery display that covered the walls of the entire wing operations center planning area. Of particular interest to the Weasel crews were the large scale charts that depicted the Red River Valley and the city of Hanoi. These maps, approximately 1:20,000 scale, were updated daily with the most recent threats, and most recent reconnaissance and strike imagery. The purpose of this threat display was twofold. First, it provided an up to date common threat picture for the entire wing to plan form. Secondly, it allowed the aircrew to conduct detailed pre-mission study and "chair flying" of the mission in advance. A wild weasel flight lead noted, "if you walked slowly about six to eight feet from the walls, it was like looking at the ground from 4,000 to 10,000 feet altitude"[9] This ability to perform detailed route and target area study helped crews identify key lead-in and terrain features necessary to visually acquire known SAM and AAA sites identified through mission planning.[10]
Wing operations and intelligence personnel developed innovative techniques for keeping their threat displays as current as possible. Two examples of this were the comparison file and the strike log. The comparison file was a planning tool that consisted of a target file for each known SAM site in North Vietnam. With the assistance of the wing photo-interpreters, the file was constantly compared against newly collected strips of imagery. This allowed the wing to rapidly scan known sites for changes in the environment, and allow them to determine if SAM equipment had arrived or departed from known sites.[11]
The strike log was updated daily to reflect which SAM sites had most recently been struck. Based on the principle that the North Vietnamese would normally move their SAM equipment each evening, the strike log was used to plan strikes against the sites which had been struck least recently. This served to harass the North Vietnamese air defenders as they moved their SAM equipment around from site to site like the carnival shell game.[12]
Although orders of battle were kept and updated at many levels of command, the orders of battle that Wild Weasel crews trusted most were the threat displays maintained by their own wing operations center. Local orders of battle incorporated the best reporting from higher headquarters in addition to the most recent aircrew derived intelligence from their own wing, or from sister wings. The informal relationships and information sharing among Wild Weasel crews and other airframes support assets, specifically the EB-66s and their six man crews, helped to build rapport and a better understanding of the threat disposition in North Vietnam.[13]
The following dialogue between Wild Weasel pilot Glenn Davis and his EWO Kevin "Mike" Gilroy, both assigned to the 355th FW at Takhli AB is illustrative of the detailed understanding the Wild Weasel crews developed of the North Vietnamese IADS:
EWO: Weak SAM at our 11 o'clock position, Glenn
Pilot: Roger. It is probably that site just south of Hoa Binh. That's the one that hammered those guys from Korat yesterday. Let's go pay him a visit.[14]
This short dialogue encapsulates the value of aircrew derived intelligence. The crew detected an active SAM, and rapidly correlated it to a known site in the vicinity of Hoa Binh. The crew made this correlation by comparing observed activity to mission materials (annotated maps carried on kneeboards) that were produced during mission planning and carried in the cockpit. The crew knew the site was responsible for the shoot- down of a 388th Fighter Wing crew the day before, and would have also been aware of the details concerning the shoot-down as well as the disposition and evasion status of the downed crew. This understanding was derived from the continuously updated SAM order of battle, from tactical details captured during the previous days intelligence debriefing and reported both laterally and to higher via OPREP. This information would have been summarized and briefed during the morning pre-mission brief at Takhli.
Understanding Threat System Capabilities
Understanding where the SAMs were was only part of the fight. Wild Weasel crews needed an in-depth understanding of the capabilities of the SA-2 Guideline in order to maximize the lethality of Weasel tactics, and increase the survivability of the strike force. Developing an understanding of SA-2 capabilities required a synthesis of both aircrew derived intelligence and technical intelligence collected on the SA-2 missile, the Fan Song radar, and the signals associated with both.
As noted in chapter 2, the avionics used by the Wild Weasel platforms detected and exploited the tracking and guidance signals associated with the Fan Song. The collection and analysis of these signals was a primary focus for both the National Security Agency and the Central Intelligence Agency. This allowed both intelligence agencies to watch for any potential changes or modifications to the SA-2 system. These strategic collection efforts would yield tactical dividends through improved detection and signal discrimination by Wild Weasel avionics, and more effective use of jamming techniques by Air Force ECM pods and systems.
In the fall of 1965, the Central Intelligence Agency conducted a creative intelligence operation to better understand the uplink, downlink, and proximity fusing signals associated with the SA-2.[15] The collection of these signals had been problematic, as they were relatively low power signals, and very directional in nature. This prevented effective standoff collection. In order to collect the target signals, the CIA planners intended to use an unmanned Ryan 147E drone as a target for North Vietnamese SA-2 battalions. The project, Operation United Effort, took place on four occasions between October 1965 and February 1966. United Effort used a modified Ryan 147E reconnaissance drone launched from a DC-130 mother ship. The drone contained radio receivers to record and retransmit all signals detected in the expected uplink, downlink, and proximity fuse frequency ranges . These signals were then retransmitted from the Ryan drone to an orbiting RB-47H ELINT aircraft, on temporary duty from the 55th Reconnaissance Wing. The RB-47H orbited over the Gulf of Tonkin, and was prepared to record any signals relayed by the Ryan drone. The first three efforts were unsuccessful, but the fourth United Effort mission on 13 February 1966 resulted in the successful collection of uplink, downlink, and proximity signals. The exploitation and analysis of the uplink signals helped refine the operation of the Wild Weasel WR-300 Launch Warning Receiver which provided a key component of threat warning for strike packages. Additionally, exploitation of the downlink signal would later be used by the B- 52 community, which began the use of downlink jamming as a standard defensive counter-tactic.[16]
In 1968 aircrew began reporting that North Vietnamese SA-2s were demonstrating an ability to engage targets lower than the previous observed 3,000 ft minimum altitude. USAF intelligence personnel suspected that the North Vietnamese had developed a more capable low-altitude improvement for the SA-2. Later that year a low- altitude Buffalo Hunter drone mission imagery of an SA-2 site revealed a white cubicle mounted on top of the Fan Song antenna set. The nature of the cubicle was unclear at first, but was later determined to be part of an optical sighting system. This imagery, combined with the aircrew derived intelligence reporting, helped intelligence analysts determine that the North Vietnamese were in fact operating the Fan Song-F upgrade, which provided an optical tracking and engagement capability for the SA-2.[17]
This development was particularly relevant to Wild Weasel crews as the optical capability allowed the North Vietnamese operators to track and engage without emitting the normal Fan Song tracking signal, and effectively decreased engagement warning time.
Understanding Threat Tactics
Aircrew derived intelligence was especially critical for building an understanding of enemy threat tactics. Unlike traditional intelligence collection, often collected from standoff platforms, the intelligence derived from Wild Weasel crews was particularly important both due to the amount of time spent in the threat area, as well as the amount of interaction that the Wild Weasels had with the North Vietnamese IADS. The Wild Weasel's unofficial motto, "First in, Last Out" referred to the fact that the Weasel crews spent the most amount of time in the highest threat areas including the Red River Valley.[18] Wild Weasel crews often spent up to 35 minutes of vulnerability time in a Route Pack VI target area as they suppressed the North Vietnamese SAMs.[19] This amount of threat exposure gave the Wild Weasel crews a unique perspective into North Vietnamese SAM tactics.
By May 1966, aircrew debriefings had revealed a shift in North Vietnamese SAM tactics. In response to the introduction of the Wild Weasel mission and the Shrike ARM, the North Vietnamese began more tail aspect, or rear quarter, SAM engagements.[20] This practice, while not as accurate or effective as frontal engagements, allowed the North Vietnamese to increase survivability against the Wild Weasel force. By engaging from the rear quarter, the Wild Weasels were less likely to see the SAM launch and visually acquire the SAM site.[21]
Another tactic noted by the Wild Weasel crews was the use of false launches to force strike aircraft and Wild Weasels alike to react. This technique consisted of the Fan Song emitting bursts of the missile guidance signal, without actually having a missile in flight. The advantage of this tactic was that strike packages, convinced that they were being launched at, would begin to maneuver and potentially to jettison ordnance. This led to increased importance of the Wild Weasel's ability to declare valid launches and advise the strike force to "take it down" when being engaged.[22] This level of tactical understanding was only produced through the careful debriefing, reporting, and analysis of aircrew derived intelligence.
Understanding Threat Integration
Following introduction of the Shrike missile, the Wild Weasel crews were among the first to note significant changes in North Vietnamese SAM tactics. These changes were representative of increased threat integration throughout the North Vietnamese IADS. First, Weasel crews noted decreased emission times from Fan Song radars.[23] Additionally, when Fan Songs did emit, they tended to only transmit in high pulse repetition frequency. By transmitting in HPRF only, the radar crew suffered from decreased range, but with the added benefit of providing decreased tactical warning to Wild Weasel aircraft, escorts, and strikers. Both advances--increased emission control, and selection of HPRF only—indicated an increase in centralized IADS cueing and integration.
Fusion Efforts
From its inception, the Wild Weasel program benefitted from a multi-discipline, interagency approach. With its creation from the Air Staff Task Force on SAMs in Southeast Asia, the USAF made a concerted effort to bring together the best talent from within the military, the intelligence community, and industry.[24] Following the initial Task Force meetings, the first anti-SA-2 symposium took place at Eglin AFB. This laid the groundwork for continued efforts at interagency fusion supporting the SAM suppression
mission.[25]
The first fusion effort, which began in October 1965, was the Anti-SAM Combat Assistance Team (ASCAT). The first ASCAT team was established at the 388th Fighter Wing, Korat Air Base, in support of the fledgling Wild Weasel program, and continued throughout the rest of the war. ASCAT existed primarily to provide technical assistance to tactical units, and was a field element that worked for the Tactical Air Warfare Center.[26] Although ASCAT initially supported only the Wild Weasel mission, it later grew to encapsulate other tactical electronic combat issues including support for ECM pods used by the majority of USAF fighter aircraft starting in 1966.[27]
The ASCAT teams consisted of both a pilot and an EWO, and operated as part of the wing commander's staff. The ASCAT members did not fly with the wing, they were there as non flying staff members, with all of their time and effort devoted to the execution of their ASCAT responsibilities. ASCAT provided a direct link, through 7th Air Force, back to the Tactical Air Warfare Center and the multitude of organizations in the continental United States that supported the entire anti-SAM mission. ASCAT officers provided expertise and liaison in all areas that touched on anti-SAM issues including, "providing systems improvement reports, monitoring of RHAW gear, pod improvements, new methods for dispensing chaff, analysis of combat tactics, as well as others."[28]
ASCAT officers would attend each and every mission mass briefing, and also attended all of the separate flight intelligence debriefings, as well as the Wild Weasel flight debriefing. ASCAT members were interested in any details related to electronic warfare, as well as the particular details of SAM engagements. The SAM engagements were analyzed with the intent of discovering any potential tactics changes by the North Vietnamese, or their Russian advisors, that would negate the effectiveness of RHAW
gear or ECM pods.[29]
Each day the ASCAT team members drafted a detailed report that described the results of that day's mission, with an emphasis on electronic warfare issues. This message was addressed to multiple levels of command, and to organizations that spanned the operations, intelligence, and testing communities. These messages served to increase understanding of North Vietnamese tactics, systems, and integration throughout the anti-SAM community.[30]
A second fusion effort was Comfy Coat, which originated in October 1966. Comfy Coat was an Air Force Security Service (AFSS) effort to "develop the capability for comprehensive evaluation of Air Force EW effectiveness in Southeast Asia combat operations."[31] Air Force Security Service was the Air Force "arm" of the National Security Agency / Central Security Service, and was the cryptologic nerve center for the Air Force . The Comfy Coat charter encompassed five key focus areas: "electronic warfare support, self-protection, Wild Weasel, Anti-radiation missile operations, and radar homing and warning gear." Comfy Coat provided detailed all-source tactical analysis of specific time periods or key events. Comfy Coat reporting started in March 1967 and consisted of time-critical immediate reaction reports, and monthly summary reports.[32]
The strength of Comfy Coat reporting was the fusion of "blue force" mission data including equipment characteristics, mission data, and current tactics with threat data including a detailed enemy order of battle, as well as top-secret intelligence reporting. Like ASCAT, Comfy Coat provided liaison officers at the flying wings in Thailand and Vietnam as a field extension of the Air Force Security Service.[33] These officers were Air Force cryptologists, and were intimately familiar with the capabilities of both the Air Force Security Service, as well as the broader National Security Agency collection and analysis capability.
A now de-classified USAF electronic warfare summary from 1969 noted the following about these early fusion efforts:
The two primary evaluation and assistance activities, Comfy Coat and ASCAT complemented each other. The combination eventually became established at the Wings and at 7AF; a close liaison was also maintained with USAF Security Service at Kelly AFB, Texas, and with the Tactical Air Warfare Center at Eglin, Fla. What emerged was an ASCAT/EW Liaison Officer team effort—analyzing daily EW operations in detail, identifying mistakes, confirming successes, meeting periodically to discuss both, proposing improvements, and gaining insights for the future.[34]
Both programs helped shape the interagency, multi-disciplined approach used by the Wild Weasel program to mitigate the threat posed by the SA-2, and the North Vietnamese IADS. This effort is consistent with the exploitation and analysis phases of the F3EA cycle. This fusion effort was fed from the bottom up with aircrew derived intelligence, which when fused with traditional intelligence reporting, provided the Wild Weasel crews an understanding of the formidable North Vietnamese IADS that allowed them to achieve an uncomfortable air parity.
[1]Rock, 257-258.
[2]Ibid., 256.
[3]Jack Broughton, Thud Ridge (Philadelphia: Lippincott, 1969), 23.
[4]Ibid., 23)
[5]Ken Bell, 100 Missions North: A Fighter Pilot's Story of the Vietnam War (Washington, DC: Potomac Books, 1993), 161.
[6]Bell, 79.
[7]Price, 66.
[8]Sparks, 264.
[9]Ibid., 258.
[10]Ibid., 259.
[11]Pratt, 38.
[12]Ibid.
[13]Sparks, 15.
[14]Grigsby, 173.
[15]Price, 58.
[16]Ibid., 58-59.
[17]Elder 1973, xi.
[18]Rock, i.
[19]Nalty, 42.
[20]Melyan and Bonetti, 103.
[21]Ibid., 104.
[22]Price, 94.
[23]Ibid., 95.
[24]Ibid., 43.
[25]Price, 47-48.
[26]Telford, 429.
[27]Burch, 49.
[28]Ibid., 50.
[29]Telford, 433.
[30]Ibid., 434.
[31]Burch, 48.
[32]Ibid.
[33]Ibid., 49.
[34]Ibid., 50.
CHAPTER 5 CONCLUSIONS
Wild Weasel: Effectiveness and Impact on Future Operations
The United States Air Force development of the Wild Weasel force is an excellent example of a strategic level policy failure that was mitigated through aggressive innovation at the tactical level. As a matter of policy, the Air Force's overwhelming focus on nuclear weapons delivery during the 1950s and early 1960s left the tactical air forces woefully unprepared to wage a sustained air campaign against an enemy IADS armed with radar guided surface to air missiles. Despite multiple demonstrations of the lethality of the SA-2 Guideline system—including the shoot-downs of Francis Gary Powers over the Soviet Union and Maj Anderson over Cuba--the tactical fighter force was completely unprepared to deal with the introduction of the SA-2 system into the North Vietnamese IADS in the summer of 1965.
This lack of preparedness was systemic throughout the fighter force and was reflected in many ways. First, fighters lacked the necessary avionics systems to survive in a radar SAM environment. Secondly, the USAF lacked of an effective SAM suppression force to disrupt and defeat the enemy's SAM force. Finally, an overwhelming reliance on low-altitude tactics led to unsustainable losses among the fighter force. Faced with mounting losses caused by the increasingly capable North Vietnamese IADS the Air Force Chief of Staff, General John P. McConnell, took bold steps to correct decades of neglect in fighter modernization and tactics. McConnell directed the formation of a multi-disciplinary task force to address the lethal threat posed by the SA-2. McConnell appointed Brigadier General Thomas C. Dempster to chair the Air Staff Task Force on SAMs in Southeast Asia. Under Dempster's leadership this task force laid the foundation for rapid acquisition, fielding, and combat employment of platforms, systems, and tactics that eventually allowed the USAF to gain parity with the North Vietnamese IADS.
As discussed in chapter 3, the Dempster Task Force's recommendations included four key initiatives:
1. Development of a SAM suppression force
2. Development of a missile that could be fired from a fighter and home on a radar emitter.
3. Develop ECM pods for carriage on fighters to counter the SAM radars.
4. Develop a RHAW capability for all fighters.[1]
The strength of the Task Force's recommendations were that it saw the need for both defensive and offensive systems to increase strike package survivability, while concurrently holding the IADS at risk from kinetic attack. Because these recommendations were implemented as part of a comprehensive approach to countering the SA-2 threat, it is difficult to evaluate the effectiveness of the Wild Weasel force as a stand-alone entity. To make any attempt at evaluation valid, it must also consider the increase in survivability created by the fielding of ECM pods and RHAW gear throughout the fighter force.
By the spring of 1966 the USAF had fielded permanent Wild Weasel detachments at both Takhli and Korat. At the same time, the AGM-45 Shrike anti-radiation missile made its initial combat debut, and the Wild Weasel force continually refined their tactics allowing them to find, fix, and finish SA-2s. During the summer of 1966, the Wild Weasel force shifted away from hunter-killer missions and put their primary effort into the Iron Hand suppression role. Additionally, during the summer of 1966, ECM pods began to arrive at fighter wings throughout Thailand. By March 1967, enough ECM pods existed to equip every fighter aircraft operating in Route Pack VI. This led to a noticeable decrease in losses to SAMs due to the cumulative effects of Wild Weasel suppression coupled with force wide ECM pod availability.[2] (See figure 10). Another key indicator of success was the massive increase in numbers of North Vietnamese SA-2 missiles required per kill. The percentage of SAM launches resulting in kills massively decreased starting in 1966, due to the holistic effects of Wild Weasel suppression complemented by increased survivability provided by fighter ECM pods. (See figure 11).
Figure 11. Total USAF Aircraft Losses by Month over North Vietnam
Source : LtCol Robert M. Burch, PROJECT CHECO REPORT: Tactical Electronic Warfare Operations in SEA, 1962-1968 (HQ PACAF, 1969), 43.
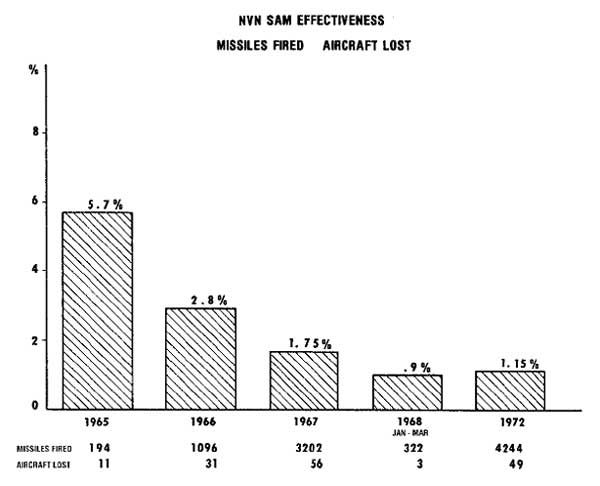
Figure 12. North Vietnamese SAM Effectiveness
Source: William W. Momyer, Airpower in Three Wars (WWII, Korea, Vietnam) (Maxwell AFB, AL: 1978), 154.
Although the USAF decreased the level of fighter attrition to an acceptable level by 1968, the USAF never gained air superiority during Operation Rolling Thunder. This failure to gain air superiority resulted in a continuous drain on resources and lives until the bombing halt of 1968. This demonstrates the limitations of SEAD--a tactical enabling mission—when the SEAD mission does not exist in the broader framework of a deliberate offensive counter-air (OCA) campaign to negate an enemy's IADS. During the Vietnam War U.S. air forces never executed a deliberate offensive counter-air campaign. The lack of a deliberate OCA campaign was due to multiple factors including excessive constraints on targeting, a fractured air component chain of command, and a lack of long term planning caused by the week to two week strike cycles executed during Rolling Thunder.
The USAF learned from its mistakes during Rolling Thunder, and buoyed by an increased focus on joint command and control spurred by the Goldwater Nichols act, the USAF executed a highly successful offensive counter-air campaign during Operation Desert Storm. Desert Storm was the first conflict fought under a single air component commander. The air component, under the leadership of Lt General Chuck Horner, himself a former Wild Weasel pilot during Rolling Thunder, planned and executed a highly effective counter-air campaign against the Iraqi IADS. This campaign was centered on paralyzing attacks against strategic command and control nodes, coupled with kinetic and electronic attack against the components of the Iraqi IADS. This campaign also included the widespread use of decoys intended to stimulate the Iraqi IADS, and allow electronic warfare forces to more easily identify Iraqi air defense systems for targeting. The key to success was that the OCA campaign attacked the IADS in both depth and breadth in order to force individual weapons into autonomous degraded operations.[3]
F3EA: Making Exploitation and Analysis a Primary Effort
The evolution of the Wild Weasel force clearly demonstrates the efficacy of the F3EA model for planning and executing SEAD. SEAD, as conducted in the 21st century is clearly rooted in the concepts and tactics first developed by the Wild Weasel I program 45 years ago. Throughout this time span the USAF has continually improved its ability to conduct the SEAD mission. The current USAF SEAD platform, the F-16CM, provides a unique capability to find, fix and finish SAMs using the Harm Targeting System sensor. Elements of F-16CMs, working in concert with electronic support and electronic attack platforms in the SEAD package, can communicate via Link 16 data link to cooperatively find and fix mobile SAMs. Additionally, F-16CMs can carry advanced targeting pods giving SEAD elements flexibility in the "Finish" phase- via suppression with the AGM- 88 High-speed anti-radiation missile, or via engagement with inertially aided munitions including the GBU-31 or GBU-38 joint direct attack munitions. The advances made in the find, fix, and finish phases are clearly remarkable.
The one area that has lagged behind the most is the ability to exploit and analyze aircrew derived intelligence. The OPREP of the Rolling Thunder campaign has been replaced by the mission report (MISREP) of the 21st century, but the product has fundamentally stayed the same. MISREPs are the only permanent record of a mission, and the information in the MISREP is critical to building an understanding of the threat. Despite massive advances in technology, the intelligence debriefing process still requires significant amounts of time spent on data capture during the debrief. This precious debrief time would be better spent focusing on the tactically significant aspects of the mission to better understand the threat and evaluate mission effectiveness. To make exploitation and analysis more meaningful, combat aircraft require a common mission recording system. Such a system would allow the automatic capture of significant events- weapons employment, signals recorded by onboard electronic combat systems, and the myriad of other details that are currently captured manually by reviewing combat mission tapes during intelligence debrief. By automating this process, and superimposing this data on a global positioning system derived "trail," the wing level intelligence effort will benefit from higher fidelity mission reports that include value added analysis. This improvement will help further the SEAD mission by maximizing the value of the "exploitation and analysis" phase of the F3EA model.
The Importance of an Integrated Approach to SEAD
From the beginning the USAF sought a joint, and interagency approach to tackling the challenge of SEAD. This focus has continued throughout the last 45 years. Operations personnel from both the USAF and the USN are exposed to the entire joint SEAD capability during large force employment exercises like Operation Red Flag, and the USAF Weapons School Mission Employment exercise. This allows SEAD package commanders to gain experience using the full range of joint SEAD capabilities. In the 21st century the full range of capabilities includes systems and weapons from all of the military services, support from the entire intelligence community, as well as capabilities protected under special access programs. The interagency approach has been at the heart of SEAD operations since Rolling Thunder.
The first requirement of any joint force commander is to gain and maintain air superiority. In the 21st century, this is conducted via a deliberate offensive counter-air campaign under the control of a designated joint force air component commander. Within that campaign a joint and interagency team will work to disrupt and negate an enemy's IADS in depth and in breadth. Part of that campaign will always include a SEAD package to suppress the enemy IADS by finding, fixing, and finishing the enemy's SAM force, using tactics and techniques that can be traced directly to the original Wild Weasels that deployed to Thailand in 1965.
The Wild Weasel Program as a Revolution in Military Affairs
MacGregor Knox and Williamson Murray note in their book, The Dynamics of Military Revolution, 1300-2050 that Revolutions in Military Affairs (RMAs) consist of changes across four key areas: doctrine, technology, tactics, and organization.[4] The creation and employment of the Wild Weasel force during Operation Rolling thunder is an excellent example of an RMA. The introduction of the Wild Weasel force created a new mission area--SEAD--that is now incorporated into U.S. Air Force offensive counter-air doctrine. The Wild Weasel program was necessitated by technological changes in aerial warfare, namely the introduction of the SA-2 into the North Vietnamese IADS. Likewise, the Wild Weasel project was reliant on technological changes in both avionics and weapons. The creation of radar homing and warning receivers, the introduction of ECM pods into the fighter force, and the creation of anti-radiation missile are all technological innovations that enabled the Wild Weasel mission to succeed. Wild Weasel tactical innovation occurred throughout the Rolling Thunder campaign, and continues to this day. Lastly, the Wild Weasel program was an RMA because it forever changed how strike packages were organized. The Wild Weasel force was rapidly integrated into strike packages, and the larger SEAD network continued to grow with the packaging of Wild Weasels, stand-off and penetrating jammers, and electronic support assets into the overall strike package. The Wild Weasel RMA persists to present day with the continuous evolution of doctrine, technology, tactics and organization as part of the offensive counter-air mission set.
Areas for Further Research
This thesis was specifically limited to examining the evolution of the Wild Weasel program throughout Rolling Thunder. Additional areas of research to complement this thesis are abundant. As the USAF was implementing the Wild Weasel program, the United States Navy was effectively doing the same to allow them to operate in the Navy's assigned Route Packs—including the highest threat Route Pack VIB. A comparison of the Navy's development of a SEAD force as contrasted with the USAF's fielding of the Wild Weasel force would be useful. Additionally, a comparison of the Wild Weasel acquisition program with other rapid fielding initiatives would be beneficial to helping prepare for rapid acquisition programs in the future. Lastly, a comprehensive look at the evolution of fighter squadron and wing intelligence operations from the Vietnam era through present would provide an objective look at how far squadron level intelligence operations have come over the last 45 years or perhaps demonstrate just how far we still need to go.
[1]Hewitt, 12.
[2]Pratt, 17.
[3]US Department of Defense 1993, Vol II, 132.
[4]MacGregor Knox and Williamson Murray, The Dynamics of Military Revolution, 1300-205 (Cambridge: Cambridge University Press, 2001), 7.
AGM-45 Shrike. First generation Anti-radiation missile developed by the United States Navy that was modified for employment from U.S. Air Force Wild Weasel airframes including the F-100F and the F-105F and G.
AGM-78 Standard ARM. Second generation Anti-radiation missile fielded in 1967 to improve suppression effectiveness. Improvements over the Shrike included increased range and system memory.
Alpha Strike. Large multi-aircraft strike conducted against Joint Chiefs of Staff nominated targets during Operation Rolling Thunder. Alpha strikes consisted of a mix of strike aircraft, flak suppression aircraft, surface to air missile suppression aircraft, electronic attack aircraft, and air-to-air escort flights.
Auxiliary General Intelligence (AGI). Soviet trawler manned and equipped to perform signals intelligence monitoring of U.S. activities.
Electronic Warfare. The use of or denial of the electromagnetic spectrum. Electronic warfare consists of three subcomponents: Electronic attack, or "jamming." Electronic protection which includes measures taken to defend friendly use of the electromagnetic spectrum, and Electronic support includes intelligence collection operations conducted to better characterize the electromagnetic spectrum.
Ground Controlled Intercept. The practice of using land and air based radars and radar controllers to help vector fighter aircraft towards airborne targets.
Pulse repetition frequency. The numbers of pulses per unit time emitted by a radar system. PRF is a critical parameter for understanding the capabilities and intentions of threat radar systems.
BIBLIOGRAPHY
Primary Sources Books
Anderegg, C. R. Sierra Hotel: Flying Air Force Fighters in the Decade After Vietnam. Washington, DC: Air Force History and Museums Program, 2001.
Bell, Ken. 100 Missions North: A Fighter Pilot's Story of the Vietnam War. Washington, DC: Potomac Books, Inc., 1993.
Broughton, Jack. Thud Ridge. Bantam Illustrated Edition. Philadelphia: Lippincott, 1969. New York: Bantam Books, 1985.
---Going Downtown: The War Against Washington and Hanoi. New York: Pocket Books, 1990.
Cunningham, Randall, and Jeff Ethell. Fox Two. New York: Warner Books, 1984.
Dramesi, John A. Code of Honor. New York: Warner Books.
Eubank, Taylor. Alone, Unarmed and Unafraid: Tales of Reconnaissance in Vietnam. Jefferson, NC: McFarland & Company, Inc., 1991.
McCain, John, and Mark Salter. Faith of my Fathers. New York: Random House Publishing Company, 1999.
McNamara, Robert S. In Retrospect: The Tragedy and Lessons of Vietnam. New York: Vintage Books, 1995.
Momyer, William W., Air Power in Three Wars (WWII, Korea, Vietnam). Maxwell AFB, AL, 1978. Reprint, Maxwell AFB AL: Air University Press, 2003
Newman, Rick, and Don Shepperd. Bury Us Upside Down: The Misty Pilots and the Secret Battle for the Ho Chi Minh Trail. New York, NY: Ballantine Books, 2006.
Rasimus, Ed. When Thunder Rolled: An F-105 Pilot over North Vietnam. New York: Ballantine Books, 2003.
---Palace Cobra: A Fighter Pilot in the Vietnam Air War. New York: St. Martin's Hardcover Edition, 2006.
---Palace Cobra: A Fighter Pilot in the Vietnam Air War. New York: St. Martin's Paperback Edition, 2007.
Risner, Robinson. The Passing of the Night. New York, NY: Ballantine Books, 1973.
Rock, Edward T. First In, Last Out: Stories by the Wild Weasel. Bloomington, Indiana: Authorhouse Press, 2005.
Sharp, U. S. Grant. Strategy for Defeat. San Rafael, CA: Presidio Press, 1978.
Stockdale, James B., and Sybil Stockdale. In Love and War. Annapolis, MD: Naval Institute Press, 1990.
Westmoreland, William C. A Soldier Reports. Garden City, NY: Doubleday Publishing, 1976.
Articles
Gilroy, Mike. (WW #174). "Single Ship Iron Hand" In First In, Last Out: Stories by the Wild Weasels (First Person Stories By Wild Weasel Pilots, EWOs, and Their Associates), ed. Edward T. Rock, Col., USAF (ret.), 167-177. Bloomington IN: Authorhouse Press, 2005.
Grigsby, John L. (WW #231). "In the Beginning" In First In, Last Out: Stories by the Wild Weasels (First Person Stories By Wild Weasel Pilots, EWOs, and Their Associates), ed. Edward T. Rock, Col., USAF (ret.), 29-44. Bloomington IN: Authorhouse Press, 2005.
Lamb, Allen. (WW #16). "The First Wild Weasel and the First Wild Weasel SAM Kill" In First In, Last Out: Stories by the Wild Weasels (First Person Stories By Wild Weasel Pilots, EWOs, and Their Associates), ed. Edward T. Rock, Col., USAF (ret.), 87-91. Bloomington IN: Authorhouse Press, 2005.
Rock, Edward T. (WW #185). "In the Beginning" In First In, Last Out: Stories by the Wild Weasels (First Person Stories By Wild Weasel Pilots, EWOs, and Their Associates), ed. Edward T. Rock, Col., USAF (ret.), 3-4. Bloomington IN: Authorhouse Press, 2005.
---"Wild Weasel I" In First In, Last Out: Stories by the Wild Weasels (First Person Stories By Wild Weasel Pilots, EWOs, and Their Associates), ed. Edward T. Rock, Col., USAF (ret.), 5-12. Bloomington IN: Authorhouse Press, 2005.
Sparks, Billy. (WW #330). "Iron Hand One--How to Become Disillusioned" In First In, Last Out: Stories by the Wild Weasels (First Person Stories By Wild Weasel Pilots, EWOs, and Their Associates), ed. Edward T. Rock, Col., USAF (ret.), 1322. Bloomington IN: Authorhouse Press, 2005.
---"A Typical Takhli Mission in '67" In First In, Last Out: Stories by the Wild
Weasels (First Person Stories By Wild Weasel Pilots, EWOs, and Their
Associates), ed. Edward T. Rock, Col., USAF (ret.), 361-372. Bloomington IN: Authorhouse Press, 2005.
Telford, Joe. (WW #256). "More Memories of Interesting Events During My Association with the Testing and Training of Wild Weasels" In First In, Last Out: Stories by the Wild Weasels (First Person Stories By Wild Weasel Pilots, EWOs, and Their Associates), ed. Edward T. Rock, Col., USAF (ret.), 361-372. Bloomington IN: Authorhouse Press, 2005.
Government Reports
Brynn, LT Edward P. PROJECT CHECO REPORT: Reconnaissance in SEASIA JUL 1966 - JUN1969. HQ PACAF, 1969.
Burch, LtCol Robert M. PROJECT CHECO REPORT: Tactical Electronic Warfare Operations in SEA, 1962-1968. HQ PACAF, 1969.
CIA Directorate of Intelligence. Soviet Military Personnel and Air Defense Operations in North Vietnam. Washington, DC: 1965.
Colwell, Robert F. PROJECT CHECO REPORT: USAF Tactical Reconnaissance in Southeast Asia July 69-June 71. HQ PACAF, 1971.
Department of Defense. Joint Publication 3-01. Countering Air and Missile Threats. Washington, DC: Joint Chiefs of Staff, 2007.
---Pentagon Papers, Gravel Edition. Washington, DC: Department of Defense, 1968.
Elder, Paul W. PROJECT CHECO REPORT: Buffalo Hunter, 1970-1972. HQ PACAF, 1973.
Heffron Jr., Charles H. PROJECT CHECO REPORT: Air to Air Encounters Over North Vietnam, 1 Jan - 30 June 1967. HQ PACAF, 1967.
Melyan, Wesley R.C., and Miss Lee Bonetti. PROJECT CHECO REPORT: Rolling Thunder July 1965-December 1966. HQ PACAF, 1967.
Overton, James B. Major. PROJECT CHECO REPORT: Rolling Thunder, January 1967- November 1968. HQ PACAF, 1969.
Pratt, Maj. John C. PROJECT CHECO REPORT: USAF Tactics Against NVN Air Ground Defenses December 1966 - November 1968. HQ PACAF, 1969.
Seig, Louis. PROJECT CHECO REPORT: Impact of Geography on Air Operations in SEA. HQ PACAF, 1970.
Smith, Mark E. PROJECT CHECO REPORT: USAF Reconnaissance in Southeast Asia (1961-1966). HQ PACAF, 1966.
Staaveren, Jacob Van. USAF Plans and Operations The Air Campaign Against North Vietnam. USAF Historical Division Liason Office, 1968.
Thorndale, C. William. PROJECT CHECO REPORT: Tactical Recon Photography Request/Distribution. HQ PACAF, 1969.
Weaver, Robert B. PROJECT CHECO REPORT: Air to Air Encounters over North Vietnam 1 July 1967 - 31 December 1968. HQ PACAF, 1969.
Wright, LtCol Monte D. PROJECT CHECO REPORT: USAF Tactics Against Air & Ground Defenses in SEA November 1968 - May 1970. HQ PACAF, 1970.
Secondary Sources Books
Clodfelter, Mark. The Limits of Air power: The American Bombing of North Vietnam. Bison Books Edition. New York: Free Press, 1989.
---The Limits of Air power: The American Bombing of North Vietnam. Lincoln NE:University of Nebraska Press, 2006.
Coram, Robert. Boyd: The Fighter Pilot Who Changed the Art of War, Back Bay Paperback Edition. New York: Little, Brown and Company, 2002.
---Boyd: The Fighter Pilot Who Changed the Art of War. New York: Back Bay Books, 2004.
Eschmann, Karl J. Linebacker: The Untold Story of the Air Raids Over North Vietnam. New York: Ivy Books, 1989.
Friedman, Norman. Network Centric Warfare. Annapolis, MD: USNI Press, 2009.
Grant, Zalin. Over the Beach. New York, NY: WW Norton & Company, 1986.
Hammond, Grant T. Mind of War: John Boyd and American Security. Washington, DC: Smithsonian Institution, 2001.
Hanyok, Robert J. Spartans in Darkness: American SIGINT and the Indochina War, 1945-1975. Fort Meade, MD: Center for Cryptologic History, 2002.
Hobson, Chris. Vietnam Air Losses: United States Air Force, Navy, and Marine Corps Fixed-Wing Aircraft Losses in Southeast Asia, 1961-1973. Hinckley, England: Midland Publishing, 2001.
Levinson, Jeffrey L. Alpha Strike Vietnam. Novato, CA: Presidio Press, 1989.
McCarthy, James R Rayfield, Robert E. Linebacker II: A View from the Rock. USAF Southeast Asia Monograph Series, Maxwell AFB, AL: Air University Press, 1985.
McCrea, M. M. USN, USMC, and USAF Fixed Wing Aircraft Losses And Damage In Southeast Asia (1962-1973). Washington, DC: Center for Naval Analysis
McMaster, H. R. Dereliction of Duty: Lyndon Johnson, Robert McNamara, the Joint Chiefs of Staff, and the Lies That Led to Vietnam. New York, NY: Harper Collins, 1972.
Michel, Marshal L., III. Clashes: Air Combat over North Vietnam, 1965-1972. Annapolis MD: Naval Institute Press, 1997.
---The Eleven Days of Christmas: America's Last Vietnam Battle. San Francisco: Encounter Books, 2002.
Knox, MacGregor and Williamson Murray. The Dynamics of Military Revolution, 13002050. Cambridge: Cambridge University Press, 2001.
Nalty, Bernard. Tactics and Techniques of Electronic Warfare: Electronic
Countermeasures in the air War Against North Vietnam 1965-1973. The Air Force in Southeast Asia Monograph Series, Washington, DC: Office of Air Force History, 1977.
Scutts, Jerry. Wolfpack: HuntingMiGs over Vietnam. Osceola WI: Motorbooks International, 1988.
Smith, John T. The Linebacker Raids: The Bombing of North Vietnam, 1972. London: Cassell & Co., 1988; 2000.
Sherwood, John Darrell. Fast Movers: Jet Pilots and the Vietnam Experience. New York: The Free Press, 1999.
Reardon, Carol. Launch the Intruders: A Naval Attack Squadron in the Vietnam War, 1972. Lawrence, KS: University Press of Kansas, 2005.
Scutts, Jerry. Wolf-Pack: Hunting MiGs Over Vietnam. Osceola, WI: Warner Books, Inc., 1988.
Sherwood, John Darrell. Fast Movers: American's Jet Pilots and the Vietnam Experience. New York, NY: The Free Press, 1999.
Staaveren, Jacob Van. Gradual Failure: The Air War over North Vietnam 1965-1966. Washington, DC: Air Force History and Museums Program, 2002.
Thornborough, Anthony M., and Frank B. Mormillo. Iron Hand: Smashing the Enemy's Air Defences. With Tony Cassanova and Kevin Jackson. Somerset, England: Patrick Stephens Limited, 2002; Reprint Sparkford, England: Sutton Publishing, 2002.
Thompson, Wayne. To Hanoi and Back: The U.S. Air Force and North Vietnam, 19661973. Washington, DC: Smithsonian Institution Press, 2000.
Tilford, Earl H. Setup: What the Air Force Did in Vietnam and Why. Maxwell AFB AL: Air University Press, 1991.
---Crosswinds: The Air Force's Setup in Vietnam. College Station, TX: Texas A&M Press, 1993.
Van Staaveren, Jacob. Gradual Failure: The Air War Over North Vietnam, 1965-1966. Washington, DC: Air Force History and Museums Program, 2002.
Warden, Mike. Rise of the Fighter Generals: The Problem of Air Force Leadership 19451982. Maxwell AFB, AL: Air University Press, 1998.
Werrell, Kenneth P. Archie, Flak, AAA and SAM. Maxwell Air Force Base: Air University Press, 1988.
Theses
Barker, Patrick K. "The SA-2 and Wild Weasel: The Nature of Technological Change in Military Systems." Masters Thesis, Lehigh University, Bethlehem, PA, 1994.
Brungess, James R. "Setting the Context: Suppression of Enemy Air Defenses and Joint War Fighting in an Uncertain World." Air University, Maxwell AFB, AL, 1994.
Hewitt, William A. "Planting the Seeds of SEAD: The Wild Weasel in Vietnam."
Masters Thesis, School of Advanced Airpower Studies, Washington, DC, 1992.
Young, James L. Jr. "United States Air Force Defense Suppression Doctrine, 19681972." Masters Thesis, Kansas State University, Manhattan, KS, 2008.
Articles
Casey, Aloysius, and Patrick Casey. "Lavelle, Nixon, and the White House Tapes." Air Force Magazine (February 2007): 86-90.
Drew, Dennis. "Rolling Thunder 1965: Anatomy of a Failure." Cadre Papers (1986): 59.
Flynn, Michael T., Rich Juergens, and Thomas L. Cantrell. "Employing ISR: SOF Best Practices." Joint Forces Quarterly (2008): 56-61.
Kamps, Charles Tustin. "The JCS 94-Target List." Aerospace Power Journal (2001): 6780.
Pribbenow, Merle L. "The -Ology War: Technology and Ideology in the Vietnamese Defense of Hanoi, 1967." Journal of Military History (2003): 175-200.